Recover the Tolkien Ring¶
We are faced with more decisions. Let's hear what Grinchum has to say.
Grinchum
My... Preciousesss...
Well that's a little creepy but, We can proceed through the door off to the right which is the Tolkien Ring door.
Sparkle Redberry
Hey there! I'm Sparkle Redberry. We have a bit of an incident here. We were baking lembanh in preparation for the holidays. It started to smell a little funky, and then suddenly, a Snowrog crashed through the wall! We're trying to investigate what caused this, so we can make it go away. Have you used Wireshark to look at packet capture (PCAP) files before? I've got a PCAP you might find interesting. Once you've had a chance to look at it, please open this terminal and answer the questions in the top pane. Thanks for helping us get to the bottom of this!
Objective 2: Wireshark Practice¶
The terminal is similar to the orientation. We have questions and need to provide answers. You will need to click the link from Sparkle Redberry to download the PCAP and investigate. The file is title "suspicious.pcap"
Type yes to proceed.
1. There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP?
We can open it up in WireShark and go to File > Export Object > Select an Option
Hints
Hint 1: https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/
Hint 2: We're looking for a protocol like FTP, HTTP, SMB, etc.
Hint 3: https://osqa-ask.wireshark.org/questions/35846/how-can-i-export-http-objects-via-command-line/
As seen above and going through the different exportable options. The only one with results is HTTP
Answer
HTTP or http
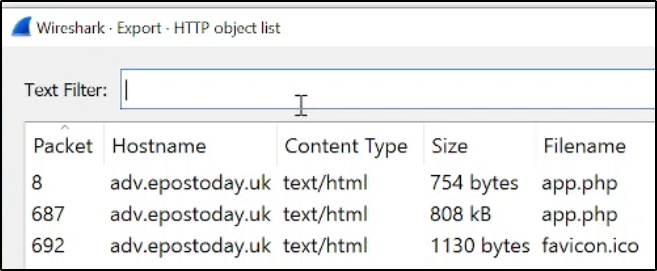
2. What is the file name of the largest file we can export?
Hints
Hint 1: https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/
Hint 2: If working in the terminal, you may need to combine tshark commands with other Linux commands
We can see from the last question that the largest file is app.php as it's 808 kB "Kilobytes" which is larger than bytes.
Answer
app.php
3. What packet number starts that app.php file?
Hints
Hint 1: In Wireshark, the Export | HTTP object list shows start packet numbers
Hint 2: When using tshark look for (text/html) in the output
We can see to the left of the file we identified previously the Packet and numbers below. This leads us to 687
Answer
687
4. What is the IP of the Apache server?
Hints
Hint 1: Search for 'apache' with Wireshark's Find function
Hint 2: Remember Linux is case-sensitive
Hint 3: Try using http.request and http.host
If you click on 687 it will select the packet in WireShark. I figured that'd be a safe place to start. You can also use frame.number == 687 to filter in the top search and only select that packet.
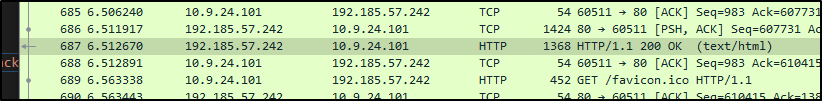
We are looking for the Apache Server's IP which would be the Source of the traffic.
5. What file is saved to the infected host?
Hints
Hint 1: Look inside the first TCP stream
Hint 2: The answer is a .zip file
Hint 3: Look inside the files that you exported using tshark
Hint 4: https://unit42.paloaltonetworks.com/wireshark-tutorial-dridex-infection-traffic/
We could follow the stream and get to this packet but, we've been on this packet for all the prior questions so, let's dig some more.
I personally just went with option one and read the script which ended in saveAs and the name of Ref_Sept24-2020.zip

6. Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by a commas ( Ex: Norway, South Korea).
Hints
Hint 1: Look up the country code
Hint 2: Look for cookies in https
Hint 3: Filter for tls handshake for certificate, https://subscription.packtpub.com/book/networking-and-servers/9781785887819/4/ch04lvl1sec27/the-ssl-tls-handshake
Hint 4: When using tshark, pipe results to grep, awk, sort, or any other tools that can help filter through the data
Hint 5: RDNSequence is the key
We know from the buildup questions we are dealing with an Apache Server. We know the ip for the Server. Let's do some more digging on the Attackers IP. This question specifically talks about TLS so, we will filter on IP and TLS. We can filter on type 11 as thats the one dealing with Certificates. You can use the :
This dwindles it down to 20 Packets that have certificates in them. Looking at each of the packets. We see a culmination of US, IL, and SS. The question asks for the full name so time for some GoogleFu. I used this link to find the full name for each.
Based on the information above we inspected the certifications noticing that the Certificate Info for the US all seem to be normal things we would expect. That leaves us with
Israel and South Sudan
7. Is the host infected (Yes/No)?
Answer
yes
This exits the terminal and we get completion notices.
Sparkle Redberry
You got it - wonderful!
So hey, when you're looking at the next terminal, remember you have multiple filetypes and tools you can utilize.
Conveniently for us, we can use programs already installed on every Windows computer.
So if you brough your own Windows machine, you can save the files to it and use whatever method is your favorite.
Oh yeah! If you wanna learn more, or get stuck, I hear Eric Pursely's talk is about this very topic.
Objective 3: Windows Event Logs¶
Dusty Giftwrap
Hi! I'm Dusty Giftwrap!
We think the Snowrog was attracted to the pungent smell from the baking kembanh.
I'm trying to discover which ingredient could be causing such a stench.
I think the answer may be in these suspicious logs.
I'm focusing on Windows Powershell logs. Do you have much experience there?
You can work on this offline or try it in this terminal.
Golly, I'd appreciate it if you could take a look.
We can interact with the terminal. Type yes to proceed.
1. What month/day/year did the attack take place? For example. 09/05/2021.
Hints
Hint 1: This is data that appears a lot in the log.
Hint 2: sort and unique are great commands.
Hint 3: Find the dates that have the highest count.
I stumbled for a few minutes greping for different things. I was like yeah just open it in Event Viewer. Looked through some lines noticed the most commands were executed during 12/24/2022. Figured, I would give it a shot based on the hints.
Which to be fair It's a "Christmas" themed even so what better way to fumble everything if you break stuff on Christmas Eve.
2. An attacker got a secret from a file. What was the original file's name?
Hints
Hint 1: https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.management/add-content?view=powershell-7.3
Hint 2: Use the output of the previous question to help narrow your choice
Well we know the attack was on the 24th from the previous question. Let's filter by that date and look through a couple events. I noticed that Event ID 4104 and Event ID 4103 was showing commands being executed. So I filtered on that narrowing the log down to 1154 versus 10k. I decided to do a little digging in those.

I start skimming through the files, Sorted by Most Recent to Oldest. I notice a command saying del .\recipe_updated.txt. My spidy senses started tingling.

We keep following the stream, we see a del .\Recipe.txt. Alright that's another trigger for me. We do a little more digging see a cat .\Recipe.txt and a $foo = Get-Content .\Recipe| %{$_ -replace 'honey','fish oil'} | Add-Content -Path `recipe_updated.txt'. Which tells me they found a Recipe file and then modified the recipe and copied the contents of recipe to another file called recipe_updated.
3. The contents of the previosu file were retrieved, changed, and stored to a variable by the attacker. This was done multiple times. Submit the last full PowerShell line that performed only these actions.
Hints
Hint 1: The desired line in the file will start with a $ since the question specifies a PowerShell variable (ex- $var).
Hint 2: To narrow your search look at https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-content?view=powershell-7.3
Hint 3: Windows logs are in reverse-chronological order, try reversing their order with tac.
Building off the previous question we might of dug a little deep ahead of time but, we see a similar command but, the LAST one has a space between $_ and -replace. It caught me off guard since I was like this is the dang command. Sent myself in a wild goose chase.
4. After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action.
Hints
Hint 1: Look for lines that start with $foo
Hint 2: Windows logs are in reverse-chronological order, try reversing their order with tac.
Hint 3: Read the question carefully, and try grepping for the answer of question 2.
We know from the past command that $foo was the variable. We see two uses of it afterwards. Looks like another mess up on the command. They used 'Recipe' on the last one so let's go with the same.
5. The attacker ran the previous command against a file multiple times. What is the name of this file?
Hints
Hint 1: Use questions 3 and 4 to help identify the file's name
The file was ran against Recipe
6. Were any files deleted? (Yes/No)
We know from initial investigation that there were files deleted.
Answer
Yes
7. Was the original file (from question 2) deleted? (Yes/No)
Hints
Hint 1: Use context clues from questions 2 and 6
I didn't like this question. I feel like that file was deleted as there was a del .\recipe_updated.txt and a del .\Recipe.txt. But, the answer was No
Answer
No
8. What is the Event ID of the log that shows the actual command line used to delete the file?
Hints
Hint 1: There are multiple Event IDs in the logs. Only one shows the actual command that was typed and ran.
Hint 2: https://linuxcommand.org/lc3_man_pages/grep1.html
Hint 3: Use output from question 6 to help modify the grep command
We sorted on this to look over all the commands that were executed already.
Answer
4104
9. Is the secret ingredient compromised? (Yes/No)
We know from investigating the commands above. The attacker replaced honey with fish oil. That'd explain the stench too.
Answer
Yes
What is the secret ingredient?
Hints
Hint 1: This answer can be found from a previous answer
We know this from previously
Answer
honey
Dusty Giftwrap
Say you did it! Thanks a million!
Now we can mix in the proper ingredients and stop attracting the Snowrog.
I'm all set now! Can you help Fitzy over there wield the Exalted Suricate?
It can be a bit mystifying at first, but this Suricate Tome should help you fathon it.
I sure hope you can make it work!
Objective 4: Suricata Regatta¶
Fitzy Shortstack
Hm? Hello...
Sorry, I don't mean to be uncharacteristically short with you
There's just this abominable Snowrog here, and I'm trying to comprehend Suricate to stop it from getting into the kitchen.
I believe that if I can phrase these Suricate incantations correctly, they'll create a spell that will generate warnings.
And hopefully those warning will scare off the Snowrog!
Only...I'm quite baffled. Maybe you can give it a go?
First Rule
First, please create a Suricata rule to catch DNS lookups for adv.epostoday.uk. Whenever there's a match, the alert message (msg) should read Known bad DNS lookup, possible Dridex infection.
We definitely want to use link that Fitzy referenced. Looking through that we piece together a command. If you ls the current directory in the terminal you will see the files previously referenced. Let's nano suricate.rules and add our command to the end of that file.
alert dns any any -> any any (msg:"Known bad DNS lookup, possible Dridex infection.";dns.query; content:"adv.epostoday.uk"; nocase; sid:1;)
./rule_checker against the file. Bingo, First rule looks good.
Second Rule
STINC thanks you for your work with that DNS record! In this PCAP, it points to 192.185.57.242. Develop a Suricata rule that alerts whenever the infected IP address 192.185.57.242 communicates with internal systems over HTTP. When there's a match, the message (msg) should read Investigate suspicious connections, possible Dridex infection
Building on the similar concepts of the last command we can use the below to trigger:
Third Rule
We heard that some naughty actors are using TLS certificates with a specific CN. Develop a Suricata rule to match and alert on an SSL certificate for heardbellith.Icanwepeh.nagoya. When your rule matches, the message (msg) should read Investigate bad certificates, possible Dridex infection
This one was a little trickier but, there is a section in the link that shows the usage of this one. Took a few various syntax fixing but, got it.
Fourth Rule
OK, one more to rule them all and in the darkness find them. Let's watch for one line from the JavaScript: let byteCharacters = atob Oh, and that string might be GZip compressed - I hope that's OK! Just in case they try this again, please alert on that HTTP data with message Suspicious JavaScript function, possible Dridex infection
Similar to above just a little research in that link on http and calling content within it. I went down a rabbit hole filtering on gzip stuff then, realized http.response_body``` can read into it.
When we completed that challenge Grinchum popped
Grinchum
Who took you, Precious? How did they take you? Mustn't happen again.
Oh, hello, humanses. Maybe we can offer help?
Yes... Grinchum will help the humanses.
We are trying to distract them from finding the rest of you, Preciouses, will talk of hints and coinses.
Have you found the coffers yet? The ones at the end of hidden paths?
There's hintses in them, and coinses, they're veerrryyy special.
Just look hard, for little, bitty, speckles or other odditities.
Don't worry, they will not look for you, Preciouses. Shhh...
Go on, humanses. Start searching!
Fitzy Shortstack
Woo hoo - you wielded Surcita magnificently! Thank you!
Now to shout the final warning of power to the Snowrog...
YOU...SHALL NOT...PASS!!!!