THM - Advent of Cyber 2022 - Day 2¶

Difficulty:
Challenge Link
OS: Linux
Things are starting to get a little more hands on with this day's challenge. We have to start a machine and go look inside of it.
Q: Use the ls command to list the files present in the current directory. How many log files are present?
Pretty straightforward, Just do as they say. Use ls and you only see a minimal amount of files.
Answer
2
Q: Elf McSkidy managed to capture the logs generated by the web server. What is the name of this log file?
Of the files provide one of them is "obvious" the file they are referencing. Take notice of the keywords web server and log file.
Q: Begin investigating the log file from question #3 to answer the following questions.
I start off by "cat filename" and it output a TON of information. I knew I'd need to use keywords for the next few questions.
No Answer Needed
Q On what day was Santa's naughty and nice list stolen?
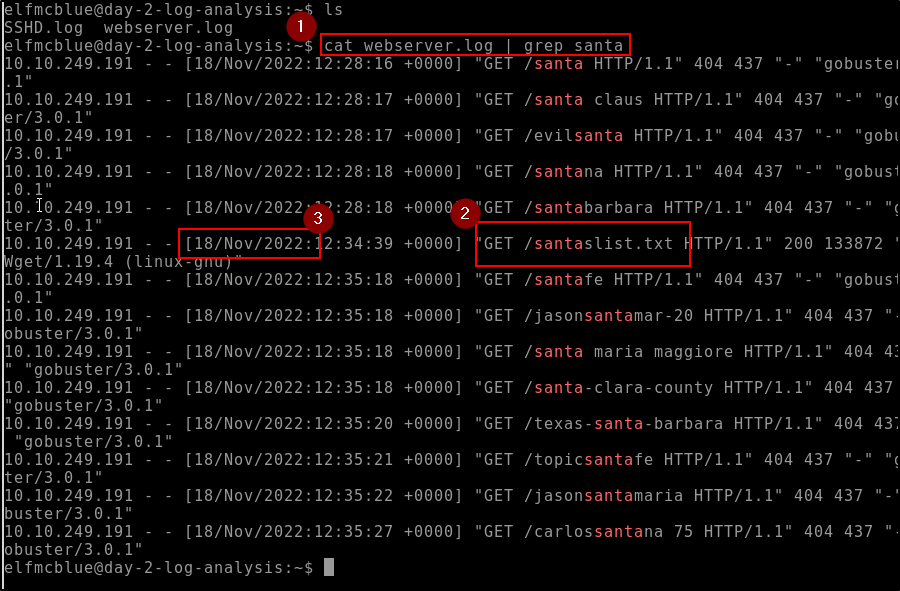
I started by cat filename | grep list which produced a large amount of findings. None of them really stood out. I decided to do "cat filename | grep santa" which produced far less responses and I was able to quickly identify a key file of the outputs listed. I looked up the date on my calendar and was able to identify the day of the week.
Q: What is the IP address of the attacker?
Reading the logs and based on the filtered findings from the command above doing a little research on how HTTP Request Logs show up you can identify the repeated IP as being the attacker's IP.
Q: What is the name of the important list that the attacker stole from Santa?
I started by cat filename | grep list which produced a large amount of findings. None of them really stood out. I decided to do "cat filename | grep santa" which produced far less responses and I was able to quickly identify a key file of the outputs listed.
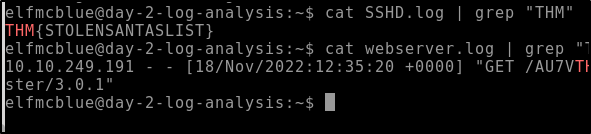
Q: Look through the log files for the flag. The format of the flag is: THM{}
This was pretty straight forward. I grepped on the first file and found nothing based on the THM Flag. Grepped the second file and boom.
Q: Interested in log analysis? We recommend the Windows Event Logs room or the Endpoint Security Monitoring Module.
No Answer Needed