Recover the Cloud Ring¶
Objective 11: AWS CLI Intro¶
Jill Underpole
Umm, can I help you?
Me? I'm Jill Underpole, thank you very much.
I'm working on this here smoke terminal.
Cloud? Sure, whatever you want to call it.
Anyway, you're welcome to try this out, if you think you know what you're doing.
You'll have to learn some basics about the AWS command line interface (CLI) to be successful though.
We interact with a terminal and follow the prompts. Type aws help.
Next were asked to use aws configure:
elf@6418d5e85446:~$ aws configure
AWS Access Key ID [None]: AKQAAYRKO7A5Q5XUY2IY
AWS Secret Access Key [None]: qzTscgNdcdwIo/soPKPoJn9sBrl5eMQQL19iO5uf
Default region name [None]: us-east-1
We can reference the link or help to see that
get-caller-identity produced the information their wanitng.
elf@f7e01c59d5cc:~$ aws sts get-caller-identity
{
"UserId": "AKQAAYRKO7A5Q5XUY2IY",
"Account": "602143214321",
"Arn": "arn:aws:iam::602143214321:user/elf_helpdesk"
}
elf@f7e01c59d5cc:~$
Answer
follow the prompts. aws configure and aws sts get-caller-identity
Jill Underpole
Wait, you got it done, didn't you?
Ok, consider me impressed. You could probably help Gerty, too.
The first trick'll be running the Trufflehog tool.
It's as good at sniffing out secrets as I am at finding mushrooms!
After that, it's just a matter of getting to the secret the tool found.
I'd bet a basket of portobellos you'll get this done!
Let's move on down the ladder to the left. Looks like we seen another hidden spot.
Objective 12: Trufflehog Search¶
Sulfrod
Hey! You - come here!
You look like someone who knows how to do this nerd stuff.
I need my terminal to be stronger, like me!
flexes
You're gonna do that for me so I can bust into this cloud machine thing.
Terminal Task 1
Use Trufflehog to find credentials in the Gitlab instance at https://haugfactory.com/asnowball/aws_scripts.git.
Configure these credentials for us-east-1 and then run:
$ aws sts get-caller-identity
Took me a little to realize TruffleHog was a tool similar to GitGuardian that checks for Secrets in Git Repos. Let's clone the repo then, run Trufflehog against it.
Oh nice we found some Secrets. Let's checkout that commit and see what they are. Bingo!
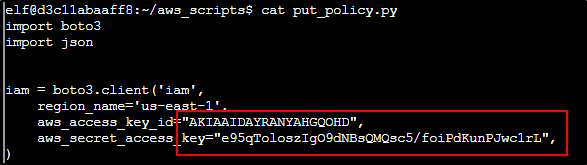
We can run
aws configure and pass those secrets into it. Objective 13: Exploitation via AWS¶
Terminal Task 2
Managed (think: shared) policies can be attached to multiple users. Use the AWS CLI to find any policies attached to your user.
The aws iam command to list attached user policies can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html
Hint: it is NOT list-user-policies.
Well the help command is your friend combined with grep. Seems like I got three options.
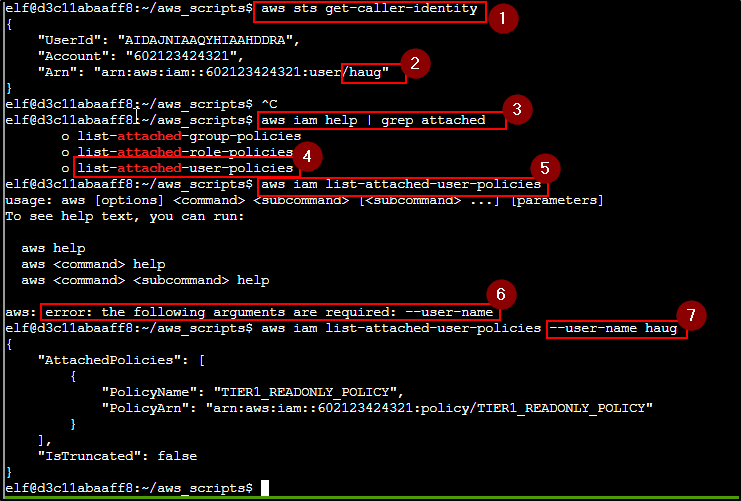
Terminal Task 3
Now, view or get the policy that is attached to your user.<br>
The aws iam command to get a policy can be found here:<br>
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html<br>
Based on the information from previous section, I checked a few different services. Ended up using the policy-arn to get it to produce tangible results.
Terminal Task 4
I had to do some reading to find out that if you pass v1 to the version it'll show the default.Task 5
Inline policies are policies that are unique to a particular identity or resource. Use the AWS CLI to list the inline policies associated with your user. <br>
The aws iam command to list user policies can be found here:<br>
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html<br>
Hint: it is NOT list-attached-user-policies.<br>
Terminal Task 6
Now, use the AWS CLI to get the only inline policy for your user. <br>
The aws iam command to get a user policy can be found here:<br>
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html<br>
Answer
aws iam get-user-policy --user-name haug --policy-name S3Perms
Terminal Task 7
The inline user policy named S3Perms disclosed the name of an S3 bucket that you have permissions to list objects. <br>
List those objects! <br>
The aws s3api command to list objects in an s3 bucket can be found here:<br>
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/s3api/index.html<br>
aws s3api help and scanned through it for list-object
Terminal Task 8
Terminal Task 9
Lambda functions can have public URLs from which they are directly accessible.<br>
Use the AWS CLI to get the configuration containing the public URL of the Lambda function.<br>
The aws lambda command to get the function URL config can be found here:<br>
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/lambda/index.html<br>
help pages
Let's hear what Sulfrod has to say and off to the next area.
Sulfrod
Ha! Now I have the ring!
This computer stuff sure is easy if you just make someone do it for you.
Wait.. the computer gave you the ring? Gah, whatever.
This never happened, got it? Now beat it, nerd!
Brozeek
Cro! Slicmer got me on the BSRS pre-sale!
Now all we gotta do is swap outfits, then you can go back in there as me.
Tell Slicmer you lost your wallet key, so you made a new wallet and need to add it to the list.
Then give him your wallet address, and we'll both be able to buy an NFT!
Social engineering at its finest, Cro.
Crozag
Bro, you usually have good ideas, but this one is really terrible.
Manipulating friends with social engineering isn't cool, Bro.
Let's do it!