THM - Advent of Cyber 2022 - Day 11¶

Difficulty:
Challenge Link
OS: Linux/Windows
This challenge is focused on doing Memory Forensics.
To access the memory dump, you will need to deploy the machine attached to this task by pressing the green "Start Machine" button located at the top-right of this task. The machine should launch in a split-screen view. If it does not, you will need to press the blue "Show Split Screen" button near the top-right of this page.
Volatility and the memory file (named workstation.vmem) is located in /home/elfmcblue/volatility3.
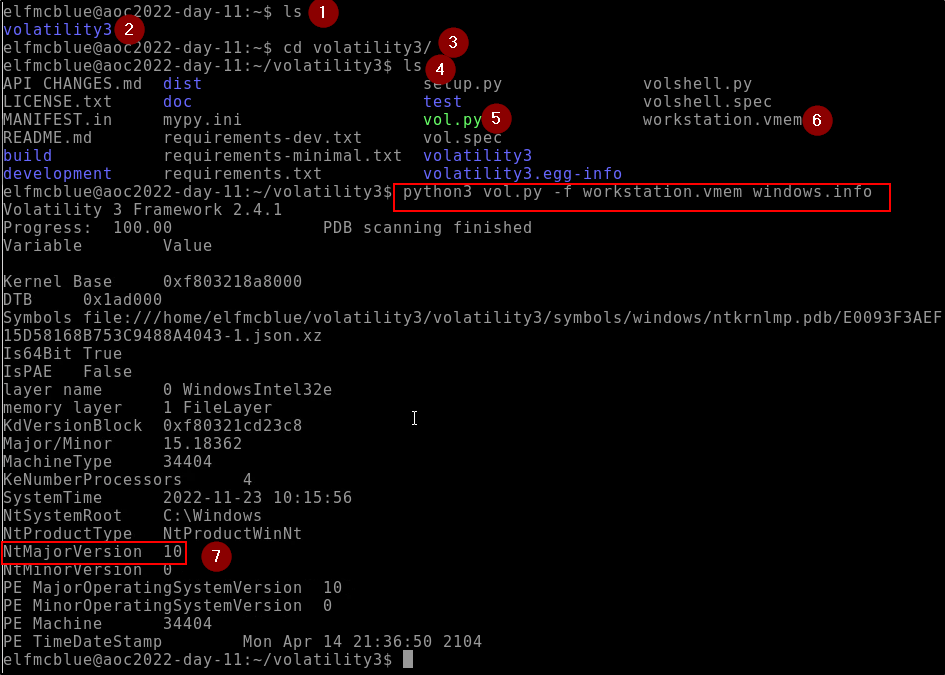
What is the Windows version number that the memory image captured?
Note: this initial scan may take up towards 10 minutes to complete. Why not grab some water or stretch your legs? We can leverage the below command to check for the version of the memory image captured.
Answer
10
What is the name of the binary/gift that secret Santa left?
We can run the below commands to use Volatility to check for the process list and then what each process is doing on the machine.
We were able to scan through the output and see a process that is out of the ordinary or something to at least take a look at.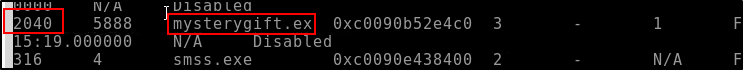
Answer
mysterygift.exe
What is the Process ID (PID) of this binary?
The PID is to the far left of the Process Name above
Answer
2040
Dump the contents of this binary. How many files are dumped?
We know the PID above, so now we can dump the files of it using the below command.
We can read over the information. See that each line of content starts withImage. So since I am lazy let's use grep and wc to get our count of files/lines that are dumped.
Answer
16 If you got 20 that's because the first 4 lines are the initial output hence, why we chose to grep on Image.

