Journey to OSCP¶
░▀▀█░█▀█░█░█░█▀▄░█▀█░█▀▀░█░█░░░▀█▀░█▀█░░░█▀█░█▀▀░█▀▀░█▀█
░░░█░█░█░█░█░█▀▄░█░█░█▀▀░░█░░░░░█░░█░█░░░█░█░▀▀█░█░░░█▀▀
░▀▀░░▀▀▀░▀▀▀░▀░▀░▀░▀░▀▀▀░░▀░░░░░▀░░▀▀▀░░░▀▀▀░▀▀▀░▀▀▀░▀░░

How Did this Journey Begin?¶
In 2019 I met a Penetration Tester that worked with me in a local Managed Service Provider. He mentioned the certification and it could open doors for me. I was always daunted by pursuing it and the cost always tended to steer me away from an attempt. I would continue on to obtain 20 other certifications as I progressed through multiple positions such as System Administrator, Information System Security Officer, Information Systems Security Manager, Cloud Architect, and Cloud Infrastructure Automation Architect. The certifications I hold are:
| Certification Name | Certification Name |
|---|---|
| Certified Info. Sys. Sec. Prof (CISSP), 2022 | Security+ CE, CompTIA, 2019 |
| eLearn Sec. Jr. Penetration Tester v1, 2022 | Network+ CE, CompTIA, 2019 |
| Terraform Associate, HashiCorp, 2022 | Technical Specialist I, Datto, 2019 |
| Gitlab Associate, Gitlab, 2022 | Network Infrastructure Prof., CompTIA, 2019 |
| SecDevOps Professional, DevOps Inst., 2022 | Secure Infrastructure Spec., CompTIA, 2019 |
| Docker Practitioner, Booz Allen, 2022 | IT Operations Specialist, CompTIA, 2019 |
| Cloud Practitioner, AWS, 2021 | Technical Specialist II, Datto, 2019 |
| IT Associate, Linux Foundation, 2021 | Switchvox Sales Engineer, Digium, 2019 |
| Certified Ethical Hacker, EC-Council, 2021 | Switchvox Support Engineer, Digium, 2019 |
| Server+, CompTIA, 2019 | A+ CE, CompTIA, 2017 |
Yea, it's quite a few but, over the years they've just been a byproduct of companies requiring this and that. Some people luck out and don't get stuck in the forever requiring certifications lives and some do. I also hold a Masters and Bachelors in IT and Cybersecurity. Information Technology and Cybersecurity is a field that you never stop learning. These are just byproducts of my never-ending desire to get better at my craft.
Preparation¶
Prior to obtaining a Learn Unlimited Subscription from Offensive Security I did quite a few other things. I have achieved the rank of "Hacker" on HackTheBox. I have "Owned" a total of 24 User and 20 System Owns. I have completed 10 of the challenges. I've also completed 29% of HackTheBox Academy's Penetration Tester Pathway. I really really enjoy HTB Academy's Content.
I have completed the following courses from TCM Security ( Practical Ethical Hacking, Windows Privilege Escalation, Linux Privilege Escalation, Open-Source Intelligence, and partially did Movement and Pivoting Course.) I own 90% of the TCM Academy Courses. My original intent was to take PNPT prior. I've also taken numerous Udemy Courses, and quite a few CTFs such as:
- SANS KringleCon Holiday Hack 2022 – Honorable Mention
- HTB Cyber Apocalypse 2023 CTF Rank 439th out of 6482 Teams - 2023
- HackTheBAHx X Summit CTF (13th out of 88 Teams) - 2023
- HackTheBAHx CTF [ 4th Place of 101 Teams] – 2022
- University CTF [2nd out of 50] - 2020
- Collegiate Penetration Testing Competition (CPTC) - 2019
- Individual National Cyber League [ 558th of 4149] – 2019
- Team National Cyber League [ 25th of 689] - 2019
What is Offensive Security Certified Professional (OSCP)?¶
Abstract
The industry-leading Penetration Testing with Kali Linux (PWK/PEN-200) course introduces penetration testing methodologies, tools and techniques via hands-on experience and is self-paced. Learners who complete the course and pass the exam will earn the OffSec Certified Professional (OSCP) certification which requires holders to successfully attack and penetrate various live machines in a safe lab environment. The OSCP is considered to be more technical than other ethical hacking certifications and is one of the few that requires evidence of practical penetration testing skills. Reference: https://www.offsec.com/courses/pen-200/
Workstation Specs¶
- Windows 10 x64 Pro
- i7 12th Gen
- 64 GB RAM
- 3070 Graphics Cards
Kali Setup¶
I used the most recent Kali Image for VMWare Workstation Desktop Pro. This allowed me the ability to snapshot with ease and not have to have panic attacks when the VM fails which will inevitably happen. I also feel like VMWare just runs so much more smooth on every platform and works consistently. You can get a discount if your a student using the Academia discount.
Starting Pen-200-2022¶
In January, I was made aware that my company would allow us to use our training funds to cover the Learn Unlimited Subscription for OffSec. Around that same month I was also interviewing for a Penetration Tester role and the response was a no because of specific requirements and I should pursue my OSCP. This relit my desires. Sometimes, a NO is all it takes. That same month I ALSO got selected to participate in an internal effort that helped fuel this desire. I cannot speak much on it. But, it surrounded me with like minded people who helped push me.
I completed all off Exercises around March 5th and started in the "Legacy" Labs on March 6th. I set a goal to complete 1 machine a day until March 20th. I ended up completed 24 Machines. Somewhere around that time Pen-200-2023 came out. I set these goals to really hammer home that persistence is key. I had a few people in my circles that had failed and really put a bad taste in my mouth. I ironically love a challenge. It's one the biggest motivators of my success today.
Starting Pen-200-2023¶
I completed ALL the Exercises in 2023 as well and this time I documented EVERY exercise so that I could easily reference. I caught myself needing stuff before when I went into the labs. I told myself I wasn't going to make that mistake again.
Note
Reference: https://www.offsec.com/documentation/penetration-testing-with-kali.pdf
Reference: https://www.offsec.com/offsec/pen-200-2023/
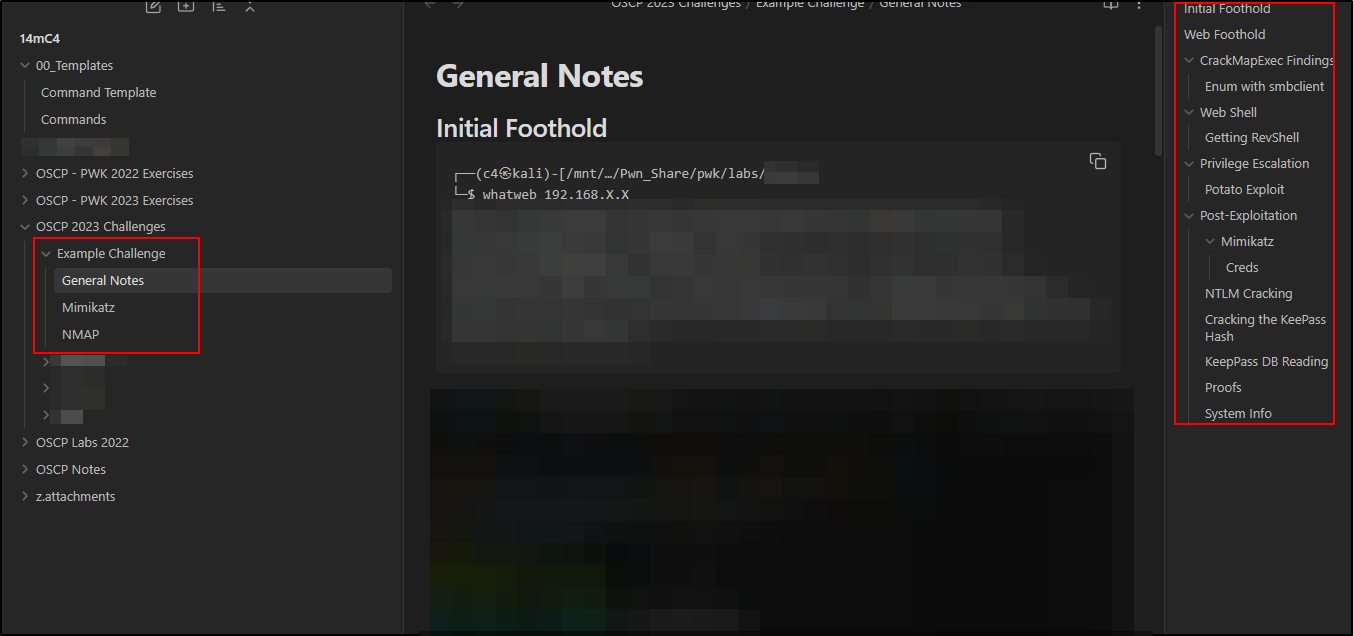
Taking Notes in the Challenges (Labs)¶
I used Obsidian to take notes. I structures my notes in a way that would make sense for writing the exam report.
Pretty much following this general guideline:
- NMAP Scans
- Initial Foothold
- POC ( Steps to Compromise )
- Privilege Escalation
- WinPEAS/LinPEAS
- POC ( Steps to Compromise)
- Post-Enumeration
- Findings
I also use the Templater plugin in Obsidian Community Plugins as shown in Siddicky's AD Walkthrough. I setup my most used commands and the front matter. SUPER useful for the Challenges, HTB, CTFs, etc.
Example Layout in my "Templated" Commands:
---
Internal Target IP = 192.168.1.1
---
## NMAP Scanning with Proxychains ( Internal IPs)
proxychains nmap -sC -sV -oN <% tp.frontmatter["Internal Target IP"] %>-initial-Nmap <% tp.frontmatter["Internal Target IP"] %>
General Kali Tips and Tricks¶
Nick's blog covers some general items that I used throughout my journey. The most prominent item being that I setup a "PwnShare" that allowed me to easily transfer files between windows and my kali instance. This folder was also backed up to my OneDrive. This meant that even when Kali failed, which I did experience a few times, that I could pick up the ball and keep playing.
Mount Shared Folder from VMWare. You will need to use Sudo.
#!/bin/bash
vmware-hgfsclient | while read folder; do
echo "[i] Mounting ${folder} (/mnt/hgfs/${folder})"
mkdir -p "/mnt/hgfs/${folder}"
umount -f "/mnt/hgfs/${folder}" 2>/dev/null
vmhgfs-fuse -o allow_other -o auto_unmount ".host:/${folder}" "/mnt/hgfs/${folder}"
done
Basically anytime I logged into my machine I just ran the quick script and started up my hacking. I stored my ovpn file in there as well for ease of use. Another useful script I had was using the Kali's Widgets to look into my PwnShare and run this script which output the Tun0 IP into my taskbar at top for ease of checking my Kali IP.
Can see in action on this Github
#!/bin/bash
# Prints the IP of the interface passed as an argument
# Example usage:
# Option 1 - With prefix to identify the network --> /home/username/ip_widget.sh tun0 🟢
# Option 2 - Just the IP --> /home/username/ip_widget.sh tun0
# It can be used to echo interface IP in xfce-genmon4 widgets (kali)
INTERFACE=$(cat /sys/class/net/$1/operstate 2>/dev/null)
if [[ "$INTERFACE" == "up" || "$INTERFACE" == "unknown" ]];then
if [ $# -eq 1 ]; then
ip -4 addr show $1 | grep -oP '(?<=inet\s)\d+(\.\d+){3}'
elif [ $# -eq 2 ]; then
echo $2 $(ip -4 addr show $1 | grep -oP '(?<=inet\s)\d+(\.\d+){3}')
fi
else
echo ""
fi
I used the following Aliases:
# ALIASES
alias vpn='sudo openvpn /c4/pwnshare/universal.ovpn'
alias webup='python -m SimpleHTTPServer 80'
alias ss='searchsploit $1'
alias ssx='searchsploit -x $1'
Working through Pen-200-2023¶
Switching over to the 2023 content was like going from night to day. This time I decided to take detailed notes of every single exercise. I found myself running into situations where I really wish I had referenced stuff. Common commands come in super handy. It was almost like a reset switch for me to really start focusing on my note taking skills.

I could list out a good 50 or so resources but, I will limit it to a few that were crucial to my success in the course.
- Super thorough writeup and review by Steflan Security. I could go into the same detail but, why. They did such an amazing job and even though the course is AMPLE you can definitely take it a step further with some his suggestions. I've done most just adhoc thorough the years of studies. Their post is a little older and less necessary for the revamp of 2023 however, it could help. They also have a lot of other good articles on the blog. Steflan Security OSCP Write-up
-
TJNull has been in the community for ages and has always had good information for the OSCP. You can find some very valuable stuff here or his Excel Sheet with HTB Like Machines. I'd argue that with the 2023 revamp the Pen-200 content can be self-sufficient but, its good to go give some of those machines a try.
TJNull's Preparation Guide -
HackTricks is an ASTONISHINGLY good resource for all things Penetration Testing. He covers so much and references so much that I tend to always start there first with a search. Something like "Port 80" and then reading up on those sections.
HackTricks -
Active Directory can be daunting but, this MindMap is super useful for helping you determine various active vectors and ways you can progress.
Orange Cyber Defence Mind Map -
GreenShot is a Windows version of FlameShot in Kali. SUPER nice tool and makes for very clean screenshots. I add borders to all my images when using it and can quickly add #s, Arrows, and Obfuscate stuff.
GreenShot
PWK Course Thoughts¶
I had the luxury of taking 2022 and 2023. I really enjoyed 2023. It was very well put together. The flow was manageable the content aligned and it just made so much more sense compared to 2022. I personally feel like the Exercises help build you up to the challenges if you take them seriously. Some people rush through the content and get to the challenges. Everyone has their style of learning but, at the end of the day anything shown in course minus metasploit has a chance to be in exam or necessary in the labs. Luckily, majority of 2023 is concepts and helps you build a methodology. It felt like Offsec is trying to make it a more comprehensive course. However, I definitely still used external resources to elaborate on other topics.
Music Playlist¶
I find myself getting into deep lofi music when studying. It keeps my mind focused and I really enjoyed listing to Vol1 and 2 of Red Siege's Playlists.
Red Seige's LoFi Playlists
Exam Day¶
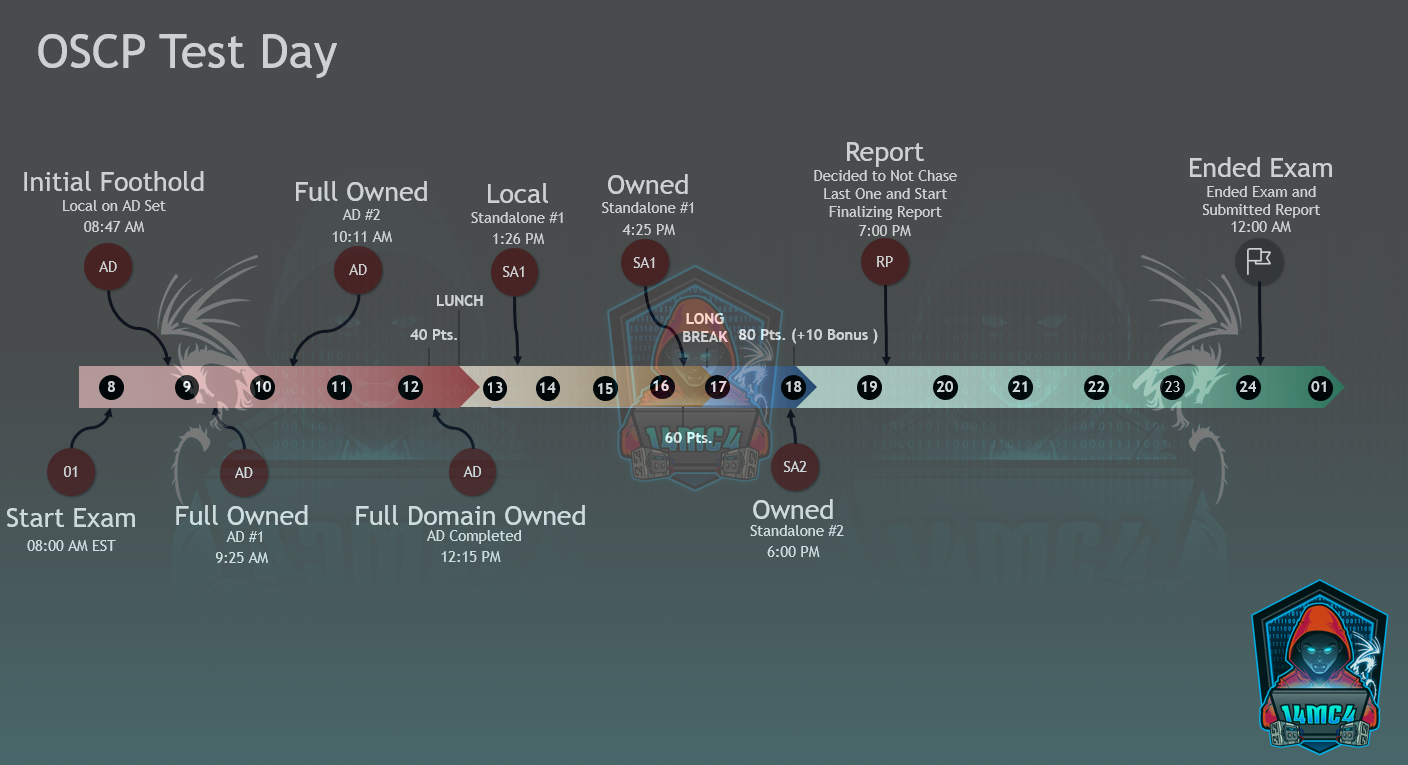
I had my 1st exam scheduled for April 30th. I got through 3/6 of the Challenges. I slept in my guest bedroom with a mediocre night of sleep. I woke up early since I could not sleep and paced around the room. I started the setup on time and soon as Im beginning to do the setup my internet starts to die and dropped to 10 mbps. Sadly, it turns out there was a storm and outage in my area. Luckily, I was able to message with Offsec on their chat platform. The Reps were insanely helpful, understanding, and really valued my experience. Compared to all the horror stories I've read over the years I was quite happy. They got me rescheduled without having to burn one of my attempts.
I was able to schedule for the 2nd of May and this time my internet decided to play nice the whole day. I worked through the exam and just tried to stay as calm as possible. I found myself pacing, doing jumping jacks, and taking constant breaks. I did my best to eat decent. I had nature valley bars, water, and four reigns. I knew I needed to stay hydrated to pull off a long test so constantly drank water. I probably when a little overboard with the energy drinks. Another student gave me advice that really stuck with me and it was just "have fun". I took that mindset into the exam and just treated it like a challenge having fun. I was really big on the if I hit any way to step backwards and keep enumerating. I had to constantly remind myself that this is a 200 level course and to not chase the rabbits.
I did obtain authorization from Offensive Security to post my timeline in a infographic. I ended up getting around 90 Points ( 80+10 Bonus ). I could have went for the last 10 points but, I was tired and I valued finishing my report with access to labs in it's entirety.
Some Quick Tips:
- Don't Sleep on Blood Hound
- Don't be scared to use Metasploit once. I was.
- Take notes throughout the exam. It's save yourself time later.
Report Writing¶
I used SysReptor to write my report. They have templates that mimic the proposed template by Offsec. I could write in Markdown and the software easily converted for me. It took a lot of the fighting with Office products out of my way and let me focus on producing a solid report. My report ended up being about 50 or so pages.
Final Thoughts¶
I spent a countless amount of hours. I would estimate a minimum of 3hrs a day over 108 days. That would total 324 hours. Some days I for sure worked more then 3 hours and some days I did not work more then 3. I set goals and remained consistent throughout the period of time. Very much a tortoise over a long period wins the race vibe. I got heavily involved in the community helping others as I was working through the course. It helped me reinforce the knowledge gained but, at same time give back to others. I'm huge on giving back and helping others. Turns out the community noticed me. I ended up getting awarded with a Community Companion badge on the discord.
At the end of the day the common theme throughout the course was "Enumerate Harder". I found myself even telling the same thing to other students as they hit a way. Step back and make sure you enumerated. The answer might be very well in front of you.
 Reference: https://h4ck.co/oscp-journey-pwk-oscp-review/
Reference: https://h4ck.co/oscp-journey-pwk-oscp-review/

Onto OSWA, OSEP, OSWE, and OSED. Goal it to see how close I can get to OSCE3.