Journey to OSWA¶
░▀▀█░█▀█░█░█░█▀▄░█▀█░█▀▀░█░█░░░▀█▀░█▀█░░░█▀█░█▀▀░█░█░█▀█
░░░█░█░█░█░█░█▀▄░█░█░█▀▀░░█░░░░░█░░█░█░░░█░█░▀▀█░█▄█░█▀█
░▀▀░░▀▀▀░▀▀▀░▀░▀░▀░▀░▀▀▀░░▀░░░░░▀░░▀▀▀░░░▀▀▀░▀▀▀░▀░▀░▀░▀

Modified from Original - Image Credits
How Did this Journey Begin?¶
Continuing on from my previous blog post titled Journey to OSCP. I decided to take what I thought would be a good next step being that Web-200 is another 200 level course like OSCP, fairly new, and I have Learn Unlimitted. So, why not give it a shot. I already have my OSCP and multiple other certifications from various certifying bodies. I know my weakness is WebApp and what better way to start perfecting that then playing around on OSWA or OSWE. Who knows I might need to change the name to Journey to OSCE3. Some of my other goals for this year. My intentions are to
Preparation¶
I recently completed my OSCP with covered some of the topics that were covered within Web-200. Well, not as in detail but, I had an understanding going into this course. I completed the Web-200 in it's entirety including the labs.
Other than Web-200, I also started going through HTB Academy's Bug Bounty Hunter pathway but, only ended up doing 17% of it. I was honestly just trying to kill time while waiting on my exam. I scheduled it later thinking the course would of took me longer. I also started going through Burp Suite Academy which I honestly will continue even post passing OSWA. I've heard it helps build on OSWE. Can't really argue since it is around 240+ Exercises for free with quality content and videos. I only ended up doing stuff in sections that I wanted some work on which were SQLi and some Directory Traversal stuff.
What is Offensive Security Web Assessor (OSWA)?¶
Abstract
Learn the foundations of web application assessments with Foundational Web Application Assessments with Kali Linux (WEB-200). Learners who complete the course and pass the exam will earn the OffSec Web Assessor (OSWA) certification and will demonstrate their ability to leverage web exploitation techniques on modern applications. This course teaches learners how to discover and exploit common web vulnerabilities and how to exfiltrate sensitive data from target web applications. Learners that complete the course will obtain a wide variety of skill sets and competencies for web app assessments.
Reference: https://www.offsec.com/courses/web-200/
I would go on this elaborate explanation of what it's like to take OSWA, but, BLUF - 24hr Hands on Test, 24hr Report. No bonus points like OSCP and need a 70 to pass. In Theory, since they don't give our scores, I scored a 80.
Workstation Specs¶
- Windows 10 x64 Pro
- i7 12th Gen
- 64 GB RAM
- 3070 Graphics Cards
- Samsung 34-inch 4k
- Dell 34-Inch 4k Curved
- Dell 24-Inch 1080
I'm almost to the point, It may be time to do a more thorough breakdown.

Kali Setup¶
I used the most recent Kali Image for VMWare Workstation Desktop Pro. This allowed me the ability to snapshot with ease and not have to have panic attacks when the VM fails which will inevitably happen. I also feel like VMWare just runs so much more smooth on every platform and works consistently. You can get a discount if your a student using the Academia discount.
Starting Web-200¶
I started the course on May 10th and finished all of the content on June 19th. I had my exam scheduled for late July but, ended up getting bored so decided to move up to June 9th at 2am. I found some topics in the course to be quite annoying but, had some helpful students like 0x4ndy and the Student Mentors to bounce ideas off. I will say it's a culture shock to go from Pen-200 to Web-200. The flowing support from others or mentor pretty much dwindles. You definitely will be on your own for majority of the exercises unless you want to wait quite a while for responses. I took notes much like I did in Pen-200 and just built on them some more. I broke things down by Modules, Exercises, and Challenges. I also tried to start creating hitlists/checklists to run through for various items.
Taking Notes in the Challenges (Labs)¶
This is my picture from Pen-200 but, concept is the exact same for Web-200.
I used Obsidian to take notes. I structures my notes in a way that would make sense for writing the exam report. I did upgrade to Obsidian Sync with a student discount due to enjoying the tool so much and even OneDrive or other backups just dont work well for mobile. Now I can view my Vault on mobile and has made it easier for me to study. I tend to review notes, and respond to people on discord in downtime so this allows me flexibility.
I also use the Templater plugin in Obsidian Community Plugins as shown in Siddicky's AD Walkthrough. I setup my most used commands and the front matter. SUPER useful for the Challenges, HTB, CTFs, etc.
Example Layout in my "Templated" Commands:
---
Internal Target IP = 192.168.1.1
---
## NMAP Scanning with Proxychains ( Internal IPs)
proxychains nmap -sC -sV -oN <% tp.frontmatter["Internal Target IP"] %>-initial-Nmap <% tp.frontmatter["Internal Target IP"] %>
General Kali Tips and Tricks¶
Nick's blog covers some general items that I used throughout my journey. The most prominent item being that I setup a "PwnShare" that allowed me to easily transfer files between windows and my kali instance. This folder was also backed up to my OneDrive. This meant that even when Kali failed, which I did experience a few times, that I could pick up the ball and keep playing.
Mount Shared Folder from VMWare. You will need to use Sudo.
#!/bin/bash
vmware-hgfsclient | while read folder; do
echo "[i] Mounting ${folder} (/mnt/hgfs/${folder})"
mkdir -p "/mnt/hgfs/${folder}"
umount -f "/mnt/hgfs/${folder}" 2>/dev/null
vmhgfs-fuse -o allow_other -o auto_unmount ".host:/${folder}" "/mnt/hgfs/${folder}"
done
Basically anytime I logged into my machine I just ran the quick script and started up my hacking. I stored my ovpn file in there as well for ease of use. Another useful script I had was using the Kali's Widgets to look into my PwnShare and run this script which output the Tun0 IP into my taskbar at top for ease of checking my Kali IP. This has been CRUCIAL to my success in this course, when Kali dies, which it will then, I still have all my notes, scripts, etc. Also very convenient to transfer stuff from Windows to Kali and vice versa.
Can see in action on this Github
#!/bin/bash
# Prints the IP of the interface passed as an argument
# Example usage:
# Option 1 - With prefix to identify the network --> /home/username/ip_widget.sh tun0 🟢
# Option 2 - Just the IP --> /home/username/ip_widget.sh tun0
# It can be used to echo interface IP in xfce-genmon4 widgets (kali)
INTERFACE=$(cat /sys/class/net/$1/operstate 2>/dev/null)
if [[ "$INTERFACE" == "up" || "$INTERFACE" == "unknown" ]];then
if [ $# -eq 1 ]; then
ip -4 addr show $1 | grep -oP '(?<=inet\s)\d+(\.\d+){3}'
elif [ $# -eq 2 ]; then
echo $2 $(ip -4 addr show $1 | grep -oP '(?<=inet\s)\d+(\.\d+){3}')
fi
else
echo ""
fi
I used the following Aliases:
# ALIASES
alias vpn='sudo openvpn /c4/pwnshare/universal.ovpn'
alias webup='python -m SimpleHTTPServer 80'
alias ss='searchsploit $1'
alias ssx='searchsploit -x $1'
Working Through Web-200¶
I got through the content quite fast. I started on May 10th, and finished June 19th. During that time I was unable to study for 2 weeks. So all in all, The course in its' entirely is maybe 3 weeks of casual studying. I did all the challenges in the last 2 days. I honestly was expecting a longer course but, It was still generally enjoyable. There is a lot of good topics being discussed. I worked mostly out the of browser build for Burp Suite to use for proxying and Repeater stuff. Super useful. I highly highly suggest watching over the OffsecAcademy videos as well if you are a LearnOne or LearnUnlim sub holder for Web-200-OSA. I don't know if the normal 90/120 Days gets access or not. They are not the AI reading from normal videos and are staff working through and explaining stuff in more detail. Super helpful.
You will want to install SecLists. Their wordlists are super useful. Also keep in mind the wordlists covered in the material. I had never used the raft wordlists and they kinda caught me up during the Challenges/Exercises.
- Bastyn's Github has a collection of various commands and scripts that can be used during OSWA's Content. Was helpful. Same stu
-
HackTricks is an ASTONISHINGLY good resource for all things Penetration Testing. He covers so much and references so much that I tend to always start there first with a search. Something like "Port 80" and then reading up on those sections. I used it for OSCP and used it consistently for OSWA. It's such a good resource.
-
GreenShot is a Windows version of FlameShot in Kali. SUPER nice tool and makes for very clean screenshots. I add borders to all my images when using it and can quickly add #s, Arrows, and Obfuscate stuff.
-
Burp Academy was a great resource for solidifying some topics for me.
Music Playlist¶
I find myself getting into deep Lofi music when studying. It keeps my mind focused and I really enjoyed listing to Vol1 and 2 of Red Siege's Playlists.
Red Seige's LoFi Playlists, a Motivational Speeches's podcast, and various RnB,I'll slip in this Runescape Pking playlist to switch it up too on Spotify. I tend to swap between stuff to keep mood difference.
Exam Day¶
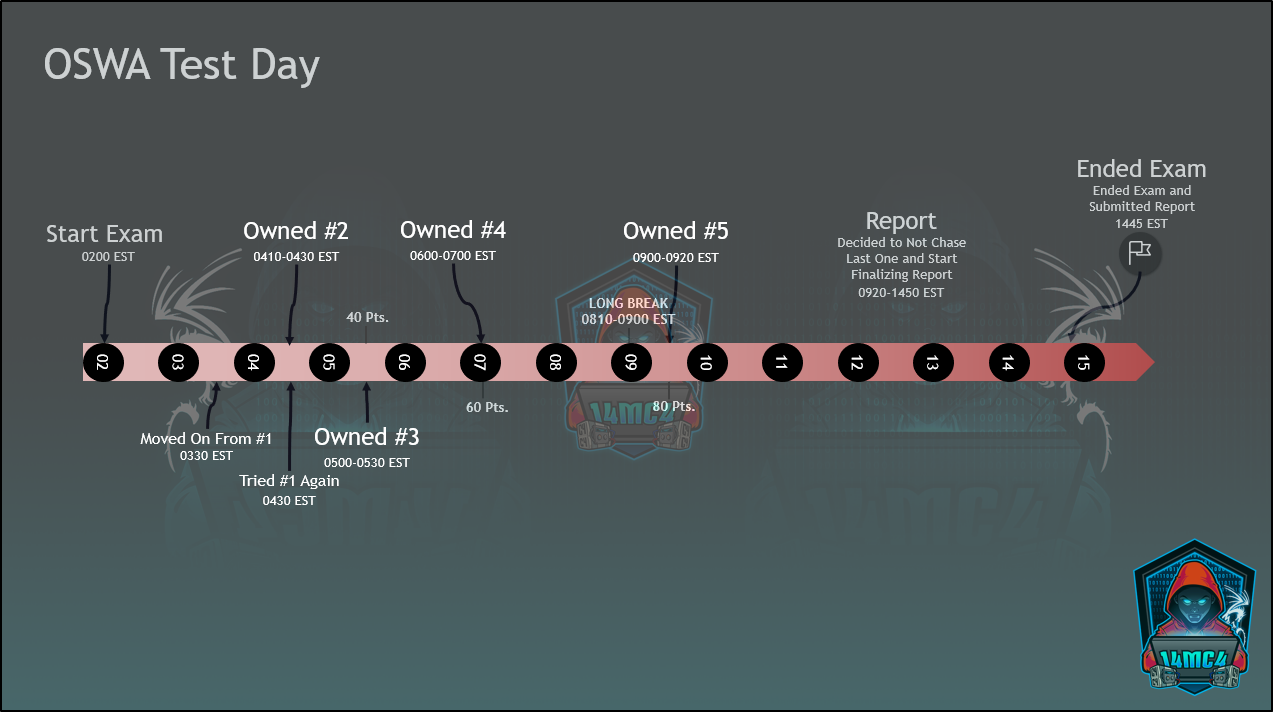
I had my first exam date scheduled for 19th June but, some real life events forced me to reschedule. I moved it to Jul 12th. Turns out I had a CTF that I got invited to participate in for work so, moved it to Jul 8th at 2am. I will say 2am wasn't entirely too bad. The kids were sleep so I did get about 7-8hrs of uninterupted time to focus. It paid off quite well. It sucked the day before but, I have an absolutely amazing wife. None of this would be possible without her support, understanding, and just all around awesome. Getting into this industry eats time and It's much like the military where time has to be sacrificed. Having a supportive family plays a huge role. However, I do take care of her too. Having that rock is crucial. She tells me all the time I never give myself enough credit for all I do but, guess its just my nature. I ended up doing everything including the report in around 12-13hrs. Im big on taking good notes as I do things which helps streamline my report. It's a good habit to get into.
How I felt getting stuck on one machine. This meme was from a CTF I did this week but, still relevant trying to find an entrypoint.
Exam Info¶
- 24 hours exam hacking
- 24 hours to write the report post exam.
- 5 machines to pwn
- Every machine has a local.txt and a proof.txt
- Maximum of 100 points
- 70 points and a valid report to pass the exam
I did obtain authorization from Offensive Security to post my timeline in a infographic. I ended up getting around 80 Points. I could have went for the last 20 points but, I was tired and I valued finishing my report with access to labs in it's entirety. I was passively enumerating #1 for multiple hours trying stuff inbetween others and just could not find my way.
Some Quick Tips:
- Take notes throughout the exam. It's save yourself time later.
Report Writing¶
I used SysReptor to write my report. They have templates that mimic the proposed template by Offsec. I could write in Markdown and the software easily converted for me. It took a lot of the fighting with Office products out of my way and let me focus on producing a solid report. My report ended up being about 60 or so pages. You can spin up a docker container locally quite quickly.
Setup all your WSL or w/e stuff
Setup for Docker¶
Normal Usage Post-Install¶
Setup FREE Offsec Template: Link¶
cd sysreptor/deploy
url="https://docs.sysreptor.com/assets/offsec-designs.tar.gz"
curl -s "$url" | docker compose exec --no-TTY app python3 manage.py importdemodata --type=design
I ended up modifying the "designs" a little more to my liking but, super sleek, super simple, and all markdown so made easy copy and paste from my notes during exams.
Final Thoughts¶
Overall, I did this post-OSCP so, a lot of the mindset and various things required for this work was already set in stone. So, it was generally not as daunting as it was for OSCP where I was starting very fresh. I enjoyed the exam, I was not a fan of the structure of some the course topics. I'm looking forward to see if they revamp more of their courses to resemble the new learning model for Pen-200.
At the end of the day the common theme throughout the course was "Enumerate Harder". I found myself even telling the same thing to other students as they hit a way. Step back and make sure you enumerated. The answer might be very well in front of you.
This quote is still quite relevant.¶
Onto OSEP, OSWE, and OSED. Goal it to see how close I can get to OSCE3.